Steps to Track Web Activity on Your WiFi
In today’s digital age, the internet is a crucial part of our daily lives. It connects us with the world, offers endless information, and provides entertainment at our fingertips. But with this great tool comes the need for responsibility, especially when it comes to monitoring what websites are visited through our WiFi networks. This is particularly important for parents wanting to safeguard their children’s online experiences, as well as employers who need to ensure their employees use the internet productively.

In this guide, we’re going to explore various ways you can keep track of the websites accessed via your WiFi network. Whether you’re looking to protect your family from inappropriate content or want to make sure your business’s internet is used effectively, understanding how to monitor this activity is key. We’ll delve into simple methods like checking your router’s history, as well as more advanced techniques involving DNS filters and parental control apps.
Our aim is to provide you with clear, easy-to-follow steps and essential tips that will empower you to monitor internet usage responsibly and effectively. So, let’s get started on this journey towards safer and more informed internet use in your home or workplace.
Understanding Router Capabilities for Website Monitoring
When it comes to keeping an eye on the websites visited through your WiFi network, your router plays a key role. Routers aren’t just for connecting to the internet; they also have features that can help you monitor online activities. By tapping into these features, you can gain valuable insights into the browsing habits of those using your network.
How to Access and Interpret Router Logs
Step-by-Step Guide:
- Locate Your Router: Find your internet router. It’s usually a small box connected to your modem.
- Login Instructions: Check the back of the router for login details. If you set it up yourself, use your credentials.
- Enter IP Address: Open a web browser and type in the router’s IP address, like 192.168.0.1 or 192.168.1.1.
- Navigate to Logs: Look for sections named ‘Advanced’, ‘Logs’, ‘Device History’, or ‘Administration’.
- Review History: Here, you’ll find a list of visited websites or IP addresses.
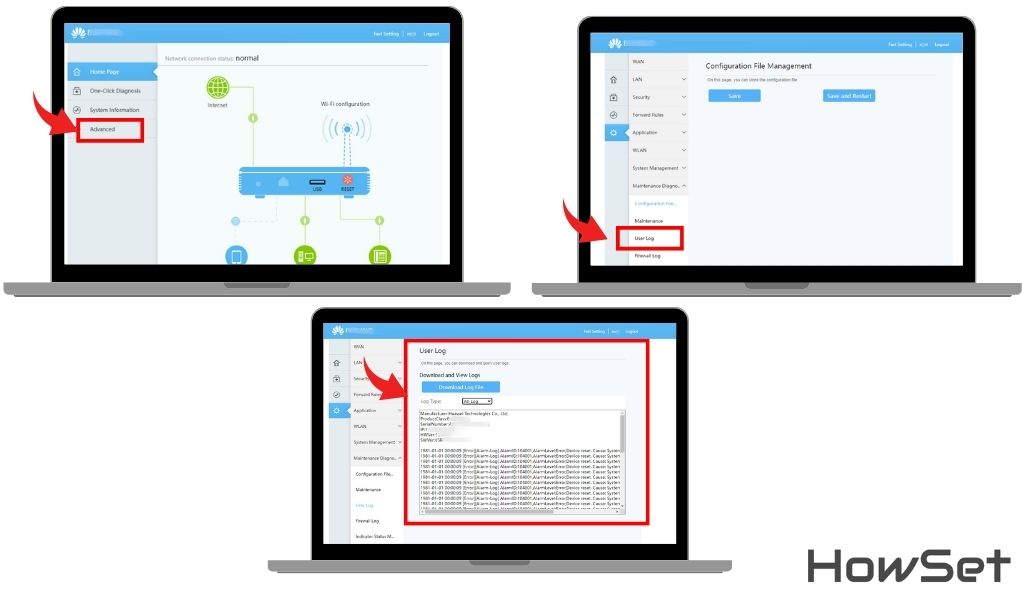
What You’ll See: Most routers show a log of IP addresses rather than specific website names. So, you might need to do a bit of research to understand which websites these IPs represent.
Enhancing Monitoring with DNS Filters
Adding a DNS filter to your home network is like having a guard at the gate, deciding which websites can be visited. DNS filters provide a more comprehensive view of web traffic and offer control over which sites can be accessed.
Advantages:
- Content Control: Block inappropriate or harmful websites.
- Real-time Monitoring: See which sites are being visited as it happens.
- User-Friendly Dashboards: Many DNS services offer easy-to-use dashboards to view and control internet usage.
Setup:
- Change DNS Settings: Redirect your router’s DNS settings to a content filter service.
- Configure Online: Follow the service’s setup guide to tailor the filtering to your needs.
Note: Keep in mind that tech-savvy users might use VPNs or proxies to bypass these filters.
By understanding and utilizing your router’s monitoring capabilities, along with DNS filters, you can create a safer and more controlled online environment for everyone using your WiFi network. This approach isn’t just about keeping an eye on the sites visited; it’s about ensuring a safe and productive online experience for all.
Utilizing Parental Control Apps for Direct Monitoring
Parental control apps are a powerful tool for monitoring the websites visited on your WiFi network, especially when it comes to ensuring your children’s online safety. These apps offer direct insight into internet usage, allowing you to see not just what sites are being visited, but also how much time is spent on them. This direct approach is particularly useful for parents who want to keep their kids away from harmful online content.
Choosing the Right App for Your Needs
Selecting the right parental control app can make a big difference. Here are some key features to look for:
- Web Browsing History: Allows you to see the list of websites visited.
- Time Controls: Set limits on how much time can be spent on certain sites.
- Content Blocking: Block inappropriate or distracting websites.
Popular Parental Control Apps:
- FamiSafe: Great for a variety of monitoring features.
- FamilyTime: Offers detailed reports and time management.
- uMobix: Good for real-time monitoring and location tracking.
Remember, the best app for you depends on your specific monitoring needs and the type of devices you’re using.
Balancing Safety and Privacy
While parental control apps are effective, it’s important to strike a balance between safety and privacy. Here are some tips:
- Open Communication: Talk to your kids about why monitoring is necessary. Explain it’s for their safety and not about mistrust.
- Respect Privacy: Avoid overly invasive monitoring. Respect their space and privacy as they grow.
- Educate about Online Safety: Teach them about the risks of the internet and how to stay safe online.
Using parental control apps wisely can help you protect your kids from online dangers while teaching them responsible internet use. It’s about guiding them, not just guarding them.
The Role of Third-Party Software in Network Monitoring
Third-party software for network monitoring can be a game-changer when you’re looking to keep an eye on the websites visited via your WiFi. This kind of software goes beyond what your router or basic parental control apps can do. It can provide detailed reports and real-time alerts about online activities. This is especially useful for businesses and tech-savvy parents who want a deeper understanding of network usage.
In-Depth Monitoring with Specialized Software
Here’s how third-party software can enhance your monitoring capabilities:
- Comprehensive Reports: Get detailed insights into internet usage, including time spent on specific sites.
- Real-Time Alerts: Receive instant notifications about access to restricted or suspicious websites.
- User-Specific Monitoring: Track internet usage by individual users or devices.
Examples of Effective Network Monitoring Software:
- NetNanny: Known for its strong content filtering and time management features.
- Qustodio: Offers a well-rounded package with time limits, web filtering, and social media monitoring.
Using these tools can provide you with a more nuanced understanding of how your WiFi network is being used.
Legal Considerations and Compliance
When using third-party software for monitoring, it’s important to keep legal considerations in mind:
- User Consent: Always ensure that users on your network are aware of and consent to monitoring, especially in a work environment.
- Data Privacy Laws: Be aware of data privacy laws in your region and ensure compliance.
- Ethical Monitoring: Use the software ethically. Focus on safety and productivity rather than invasive tracking.
Third-party network monitoring software can be a powerful tool for maintaining a safe and productive online environment. However, it’s crucial to use these tools responsibly, keeping legal and ethical considerations in mind.
Advanced Techniques: DNS Logging and Proxy Servers
For those who need more detailed information about their network’s internet usage, advanced techniques like DNS logging and proxy servers are the way to go. These methods are a bit more technical but offer a deeper dive into monitoring web activities. They are particularly useful in environments where detailed tracking and control over internet access are essential, such as in schools or large businesses.
Implementing DNS Logging for Domain Tracking
DNS logging involves keeping records of all the domain name requests made through your network. Here’s how it helps:
- Track Web Requests: See which websites are being requested by devices on your network.
- Identify Trends: Understand the most frequently visited websites and spot unusual patterns.
- Improve Network Security: Detect potentially harmful or suspicious web requests.
Steps to Enable DNS Logging:
- Access Router Settings: Log into your router and find DNS settings.
- Enable Logging: Turn on the DNS logging feature.
- Review Logs: Regularly check the logs to see the list of requested domains.
Remember, DNS logging provides data at the domain level, not the exact web pages visited.
Setting Up a Proxy Server for Comprehensive Control
A proxy server acts as a gateway between your network and the internet. It’s like having a checkpoint that monitors all web traffic.
- Total Web Traffic Monitoring: See every website request that goes through your network.
- Control Access: You can block or allow specific websites.
- Detailed Reports: Get comprehensive reports about internet usage.
How to Set Up a Proxy Server:
- Choose Proxy Software: Pick a reliable proxy server software.
- Install and Configure: Follow the setup guide to install it on your network.
- Monitor and Adjust: Use the proxy’s dashboard to monitor web traffic and adjust settings as needed.
Using DNS logging and proxy servers requires some technical know-how, but they offer unparalleled insights and control over your network’s internet usage. They are ideal solutions for scenarios where detailed monitoring and high security are priorities.
Best Practices for Responsible Monitoring
Monitoring internet usage on your WiFi network is not just about keeping track of the sites visited; it’s also about doing so responsibly and ethically. Whether you’re a parent, employer, or network administrator, it’s important to balance safety and security with respect for privacy. Applying best practices ensures that monitoring is fair, legal, and respectful of individual rights.

Balancing Security with Privacy
The key to responsible monitoring is finding the right balance between security and privacy. Here are some tips to help you achieve this:
- Inform Users: Always let users know that monitoring is in place. Transparency builds trust.
- Limit Monitoring Scope: Only monitor what is necessary. Avoid overly intrusive methods.
- Respect Privacy: Understand the importance of privacy and avoid crossing the line.
Balancing Tips:
- Clear Policies: Have clear, written policies about internet usage and monitoring.
- Purposeful Monitoring: Focus on monitoring for safety and productivity, not personal details.
- Regular Reviews: Periodically review your monitoring practices to ensure they are fair and relevant.
Keeping Data Secure and Compliant
Ensuring that the data collected through monitoring is secure and used in compliance with laws is crucial. Here’s what you need to do:
- Secure Storage: Keep the monitoring data in a secure place to prevent unauthorized access.
- Comply with Laws: Be aware of and comply with privacy laws in your region.
- Minimize Data Collection: Collect only the data you need for the intended purpose.
Compliance Checklist:
- User Consent: Obtain clear consent from users for monitoring.
- Data Protection: Use encryption and other security measures to protect the data.
- Legal Advice: Seek legal advice to ensure your monitoring practices are lawful.
Responsible monitoring is about more than just technology; it’s about using that technology in a way that respects individual privacy and adheres to legal standards. By following these best practices, you can ensure that your monitoring efforts are both effective and ethical.
Conclusion
Monitoring websites visited through your WiFi network is a valuable practice for ensuring online safety and productivity, whether it’s at home or in the workplace. From checking router logs for a general overview to utilizing advanced techniques like DNS logging and proxy servers, each method offers its own level of insight and control. It’s crucial, however, to balance this monitoring with ethical considerations, ensuring transparency with users and adhering to privacy and legal standards. By doing so, we not only protect and guide those using our networks but also foster a respectful and trustworthy online environment. Responsible monitoring, therefore, is not just about surveillance but about creating a safer, more informed, and respectful digital world for everyone.


Leave a Reply