VPN Selection: Tips and Strategies for Enhancing Your Online Privacy
In an era where our digital footprints are constantly being tracked, the importance of safeguarding one’s online privacy cannot be overstated. Every click, every search, and every website visit contributes to a vast pool of data that can potentially be exploited. As we navigate through the labyrinthine corridors of the internet, the need for a reliable shield becomes imperative. This is where Virtual Private Networks, or VPNs, step in as guardians of our online sanctity.
In this comprehensive guide, we delve deep into the world of VPNs, offering you a step-by-step journey through the nuances of selecting the right VPN service to enhance your online privacy. From understanding the fundamental mechanics of VPNs to evaluating various features and services, we aim to equip you with the knowledge to make an informed decision. Whether you are a novice user or a tech-savvy individual, this guide promises to be an enlightening read.
Understanding VPNs
The digital realm is a vast and complex network, where information travels at lightning speed. In the midst of this, VPNs stand as a bulwark, protecting your data from potential intruders and snoopers. But what exactly is a VPN, and how does it function to secure your online activities? Let’s delve deeper to unravel the intricacies of VPNs.
What is a VPN?
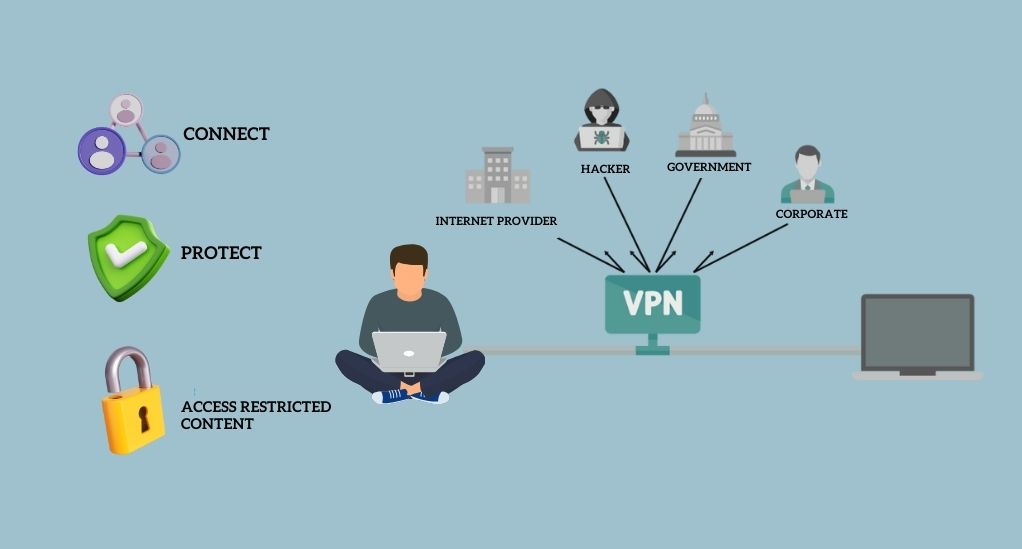
A VPN, or Virtual Private Network, is a service that creates a secure connection over the internet between your device and the website or application you are accessing. It serves as a tunnel, encrypting the data that passes through it, thereby shielding it from potential eavesdroppers and hackers. This encryption ensures that your online activities remain confidential, allowing you to browse the web with an added layer of security.
How Does a VPN Work?
At its core, a VPN works by masking your IP address and rerouting your internet traffic through a server located in a different geographical location. This process not only protects your data but also allows you to bypass geographical restrictions, granting you access to content that might be unavailable in your region. Here’s a step-by-step breakdown of how a VPN functions:
- User Authentication: Initially, the user logs into the VPN service using secure credentials.
- Secure Connection Establishment: The VPN establishes a secure connection with one of its servers.
- IP Address Masking: Your real IP address is masked, and a new IP address from the VPN server is assigned to your connection.
- Data Encryption: The data transmitted over the connection is encrypted, ensuring its confidentiality.
- Secure Browsing: You can now browse the web securely, with your data protected from potential threats.
Why is Choosing the Right VPN Essential?
Selecting the appropriate VPN is a critical step in safeguarding your online privacy. A reliable VPN service should offer robust encryption standards, a no-logs policy, and a user-friendly interface, among other features. Moreover, the right VPN can provide a seamless browsing experience without compromising on speed and performance. As we progress, we will delve into the various features and considerations that should guide your VPN selection process, helping you to navigate the digital world with confidence and security.
Key Features of a Reliable VPN
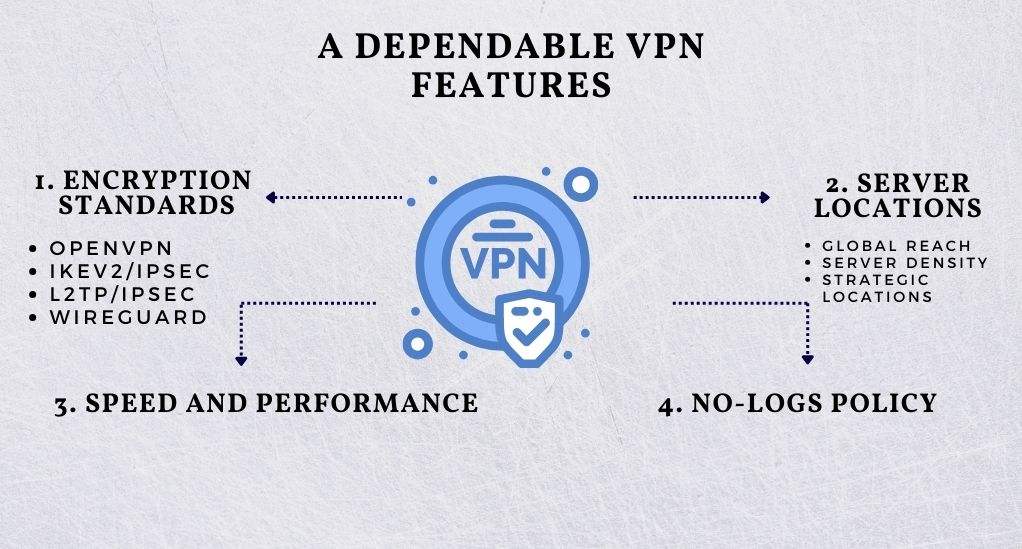
In the vast market of VPN services, distinguishing between various offerings can sometimes feel overwhelming. However, focusing on certain pivotal features can guide you in making an informed decision. Here, we dissect the essential characteristics that a reliable VPN service should embody.
1. Encryption Standards
Encryption is the cornerstone of any VPN service, acting as a fortress that safeguards your data from potential intruders. Different VPNs employ various encryption protocols, each with its unique strengths. Here, we will discuss the most commonly used protocols and their attributes:
- OpenVPN: A versatile and secure protocol that is widely used due to its strong encryption and open-source nature.
- IKEv2/IPsec: Known for its stability and security, especially for mobile users who frequently switch between Wi-Fi and mobile data.
- L2TP/IPsec: While not as secure as OpenVPN, it is commonly used for its compatibility with numerous platforms.
- WireGuard: A newer protocol that promises better speeds and improved encryption.
A comparison table illustrating the features of these protocols might look like this:
| Protocol | Security Level | Speed | Compatibility |
|---|---|---|---|
| OpenVPN | High | Moderate | Wide |
| IKEv2/IPsec | High | Fast | Wide |
| L2TP/IPsec | Moderate | Fast | Wide |
| WireGuard | High | Very Fast | Growing |
2. Server Locations
The geographical distribution of servers is a vital aspect to consider. A VPN with a wide network of servers across various regions offers better speed and the ability to bypass geo-restrictions. When choosing a VPN, consider the following:
- Global Reach: A VPN with servers in multiple countries allows for more flexible access to content worldwide.
- Server Density: More servers in a region can mean better speeds and connectivity.
- Strategic Locations: Some VPNs offer servers in regions with lenient data retention laws, enhancing your privacy further.
3. Speed and Performance
A common concern with using a VPN is the potential decrease in internet speed. However, a reliable VPN service strives to offer fast connections without compromising security. Here, we will explore tips to maintain optimal speed and performance while using a VPN.
4. No-Logs Policy
A no-logs policy is a commitment from the VPN provider that your online activities are not tracked or recorded. This policy is central to maintaining your privacy, as it prevents any potential data leakage or misuse. In this section, we will delve into the importance of a no-logs policy and how to verify a VPN provider’s claims regarding their policy.
Assessing Your VPN Needs
Before plunging into the vast ocean of VPN services available, it’s prudent to first assess your individual or organizational needs. This assessment will serve as a compass, guiding you to a VPN service that aligns perfectly with your requirements. Let’s explore the various considerations that should influence your choice.
Personal Use vs. Business Use
VPNs cater to a diverse range of users, from individuals seeking to protect their personal data to businesses aiming to secure sensitive information. Here, we delineate the distinct features that should be sought after for personal and business use:
- Personal Use:
- Privacy Protection: Shielding personal data from potential threats.
- Content Access: Bypassing geographical restrictions to access global content.
- Safe Transactions: Ensuring secure online transactions.
- Business Use:
- Data Security: Protecting business data and intellectual property.
- Remote Access: Facilitating secure access to business networks from remote locations.
- Collaborative Work: Enabling secure file sharing and collaboration.
Geographical Considerations
Depending on your geographical location, your VPN requirements might vary. Some regions impose stringent censorship laws, while others might have relaxed regulations. Here, we will discuss how to choose a VPN that caters to your geographical needs, ensuring unrestricted and secure internet access.
Device Compatibility
In a world where we are connected through a myriad of devices, a VPN service must offer cross-platform compatibility. Whether you are using a smartphone, tablet, or computer, your VPN should provide seamless protection across all platforms. In this section, we will explore the various VPN services that offer multi-device support, ensuring a uniform shield of protection across all your gadgets.
Tips for Choosing the Right VPN

Embarking on the journey to select the right VPN can be a daunting task. However, armed with the right knowledge and strategies, you can navigate this path with confidence. In this segment, we offer you a treasure trove of tips that will guide you in making an informed choice.
- Reading and Understanding Privacy Policies
A critical step in the selection process is to meticulously read and understand the privacy policies of potential VPN providers. This scrutiny will unveil the provider’s stance on data logging and sharing, helping you gauge the level of privacy they offer. Here, we will guide you on how to dissect privacy policies and identify red flags. - The Importance of a User-Friendly Interface
A user-friendly interface can significantly enhance your VPN experience. In this section, we will highlight the features that contribute to a seamless user experience, from easy setup processes to intuitive navigation. - Customer Support and Service Reliability
Reliable customer support is a hallmark of a trustworthy VPN provider. Here, we will discuss the various facets of customer support that you should consider, including responsiveness, expertise, and the availability of resources such as guides and FAQs.
Setting Up and Using a VPN
Once you’ve chosen a VPN that aligns with your needs, the next step is to set it up and integrate it into your daily online activities. This section aims to guide you through the installation process and offer tips for utilizing your VPN to its fullest potential.
Installation Process
Setting up a VPN is generally a straightforward process. Here, we will walk you through the typical steps involved in installing a VPN, from downloading the application to configuring the settings to suit your preferences:
- Choosing a Subscription Plan: Most VPNs offer various subscription plans. Choose one that suits your needs and budget.
- Downloading the Application: Visit the official website of the VPN provider to download the application.
- Installation: Follow the on-screen instructions to install the VPN application on your device.
- Setting Up Your Account: Create an account by providing the necessary details and setting up secure login credentials.
Configuring Your VPN for Optimal Performance
After installation, optimizing the VPN settings can enhance your browsing experience. This segment will guide you on how to:
- Select the best server location based on your needs.
- Choose the appropriate encryption protocol.
- Configure security features such as kill switch and DNS leak protection.
Tips for Using a VPN Safely
Using a VPN goes beyond just installing and setting it up. Here, we offer tips to ensure a safe browsing experience:
- Regularly update the VPN application to benefit from the latest security features.
- Avoid using unknown Wi-Fi networks, even when connected to a VPN.
- Be cautious while granting permissions to the VPN application on your device.
Conclusion
As we draw the curtain on this enlightening journey through the world of Virtual Private Networks, it is our fervent hope that you are now equipped with the knowledge and insight to navigate the digital seas with heightened security and privacy. In an era where our online footprints are scrutinized more than ever, adopting a robust VPN service is not just a choice, but a necessity. This guide has endeavored to be your compass, steering you through the intricate nuances of VPN selection, setup, and optimal usage. Remember, the first step towards safeguarding your online presence is being informed, and we trust that this guide has served that very purpose.
As you step forward, ready to embrace a VPN service that aligns with your needs, we encourage you to be ambassadors of online safety. Share this reservoir of knowledge with friends, family, and colleagues, fostering a community that values digital privacy and security. Moreover, we invite you to engage in a dialogue with us, sharing your experiences and insights, thereby enriching this space with diverse perspectives. Together, let’s build a digital ecosystem where privacy is not a privilege, but a fundamental right. Here’s to a safer, more secure online experience for all.


Leave a Reply