
Understanding the Role of Encryption in Blockchain Technology
In the digital age, where data is the new gold, ensuring its security, authenticity, and integrity has become paramount. At the forefront of this digital revolution is blockchain technology, a groundbreaking innovation that promises to reshape the way we think about data and its security.
What is Blockchain?
At its core, blockchain is a distributed ledger or database that records transactions across multiple computers in a way that ensures the data is secure, transparent, and immutable. Imagine a book, where each page of the book represents a block, and each block contains a list of transactions. Once a page is filled with transactions, a new page (or block) is added. Each page references the previous one, creating a linked chain of blocks, hence the name “blockchain.”
Key Features of Blockchain:
- Decentralization: Unlike traditional databases, such as a SQL database, where a single entity has control, in blockchain, every participant (known as a node) on the network has access to the entire database and the complete history of all transactions. This means no single entity has control over the data, making it decentralized.
- Transparency: All transactions are visible to anyone with access to the system. However, the identity of the person behind a transaction is encrypted, ensuring privacy.
- Immutability: Once a transaction is recorded on the blockchain, it cannot be altered or deleted. This ensures that the data remains intact and unaltered.
- Consensus Algorithms: This is a technique used to achieve agreement on a single data value among distributed processes or systems. Blockchain uses consensus models like Proof Of Work and Proof Of Stake to agree upon the validity of transactions.
Comparing Traditional Databases and Blockchain
| Feature | Traditional Database | Blockchain |
|---|---|---|
| Control | Centralized | Decentralized |
| Data Alteration | Possible | Impossible (Immutable) |
| Transparency | Limited | High (with encrypted identities) |
| Security | Central Point of Failure | Distributed & Encrypted |
Why is Blockchain Important?
The significance of blockchain extends beyond just secure data storage. It introduces a new paradigm for trust in the digital world. In traditional systems, trust is often established through intermediaries or third parties. With blockchain, trust is established through collaborative verification and advanced cryptographic techniques. This not only reduces the risk of fraud but also eliminates the need for intermediaries, making processes more efficient and less costly.
The Basics of Encryption
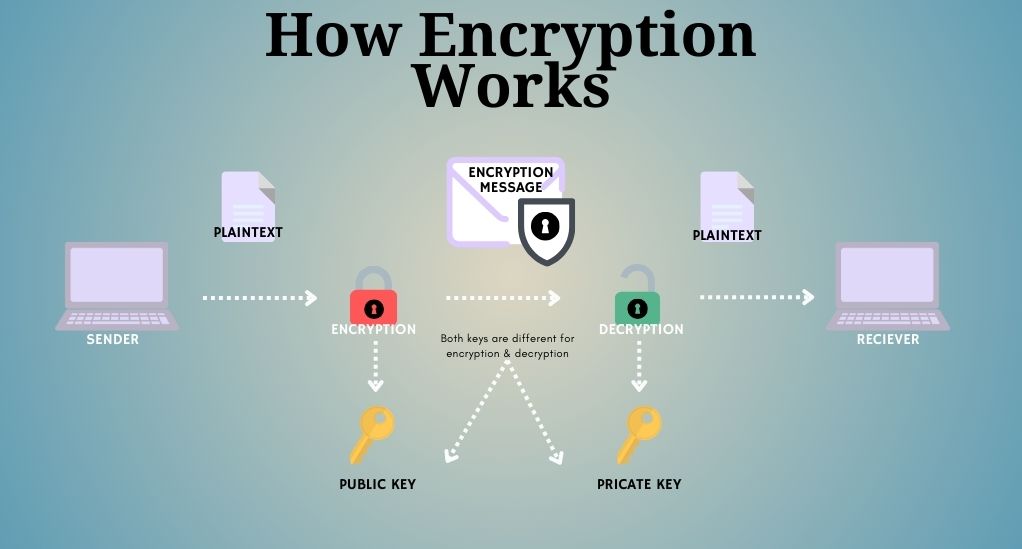
Encryption, in its simplest form, is the process of converting information into a code to prevent unauthorized access. It’s akin to a digital lock and key system, where only those with the correct key can unlock and access the information. In the realm of blockchain, encryption is the cornerstone that ensures data security and trustworthiness.
What is Encryption?
Encryption transforms readable data, known as plaintext, into an unreadable format called ciphertext using an algorithm and an encryption key. The process is reversible, meaning the original data can be restored using decryption. This transformation relies on two types of keys: public and private keys.
Public and Private Keys
- Public Key: As the name suggests, this key is public and can be shared with anyone. It’s used to encrypt data.
- Private Key: This is a secret key, known only to the owner. It’s used to decrypt data encrypted with the corresponding public key.
The combination of these keys ensures that even if someone intercepts the encrypted data, they cannot decipher it without the private key. This dual-key mechanism is known as Public Key Infrastructure (PKI).
Why is Encryption Crucial in Digital Transactions?
In the digital world, where data breaches and cyber-attacks are rampant, encryption acts as a formidable line of defense. Here’s why:
- Data Security: Encryption ensures that sensitive information, such as personal details or financial transactions, remains confidential and safe from prying eyes.
- Data Integrity: It guarantees that the data hasn’t been tampered with during transmission. Any alteration, no matter how minute, will result in a different encrypted output, signaling potential tampering.
- Authentication: Through encryption, blockchain can verify the authenticity of both the sender and the receiver in a transaction. This is vital in establishing trust in a trustless environment.
- Non-repudiation: Once a transaction is made, the involved parties cannot deny their involvement, thanks to the cryptographic proof provided by encryption.
How Blockchain Uses Encryption
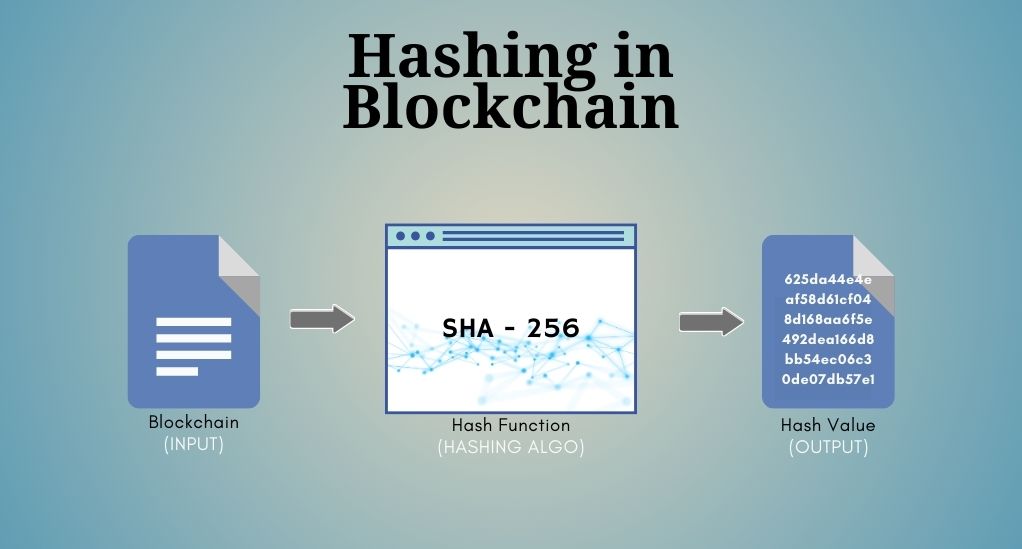
Blockchain’s revolutionary approach to data security and transparency is deeply rooted in its use of encryption. This cryptographic foundation ensures that every transaction and block added to the chain is both secure and verifiable.
Cryptographic Hashes in Blockchain
One of the primary cryptographic tools used in blockchain is the hash function. A hash function takes an input (or ‘message’) and returns a fixed-size string of characters, which is typically a sequence of numbers and letters. The output, known as the hash value or simply hash, is unique to the given input.
Key characteristics of cryptographic hashes:
- Deterministic: For a given input, the output (hash) will always be the same.
- Fast to compute: For any given data, its hash can be quickly calculated.
- Irreversible: It’s computationally infeasible to regenerate the original input value from its hash.
- Collision-resistant: Two different inputs will not produce the same hash.
- Sensitive to Initial Data: Even a minuscule change in input data will produce a vastly different hash.
In the context of blockchain, each block contains a hash of the previous block, creating an interlinked chain. This ensures that once a block is added to the blockchain, its content cannot be changed without altering all subsequent blocks, which provides security against tampering.
The Concept of Public and Private Keys
Blockchain employs asymmetric cryptography, where two keys, public and private, come into play. These keys are mathematically linked, yet knowledge of one doesn’t reveal the other.
- Digital Signatures: When a user initiates a transaction, they sign it with their private key. This signature can be verified by others using the user’s public key, ensuring the transaction’s authenticity and integrity.
- Wallet Addresses: In blockchain networks like Bitcoin, the public key is transformed into a blockchain address using cryptographic algorithms. This address becomes the user’s identity on the network, where they can receive funds.
Ensuring Data Integrity with Encryption
Data integrity is the assurance that digital information remains unaltered and uncorrupted from its original state. In the context of blockchain, ensuring data integrity is paramount, as the value of the entire system hinges on the trustworthiness of its records.
How Encryption Verifies the Authenticity of Data
Every piece of data or transaction on the blockchain is associated with a unique cryptographic signature. This signature, generated using encryption algorithms, acts as a fingerprint for the data. When data is retrieved or accessed, its signature is checked against its current state. If the data has been altered in any way, the cryptographic signature will not match, indicating a breach in data integrity.
The Irreversible Nature of Blockchain Transactions
One of the standout features of blockchain is its immutability. Once a transaction is added to the blockchain, it becomes a permanent record that cannot be altered or deleted. This is achieved through the following mechanisms:
- Chain of Blocks: Each block in the blockchain contains a reference (in the form of a hash) to the previous block. This creates a chain where each block is dependent on its predecessor. To alter a single block, an attacker would need to change every subsequent block, which is computationally infeasible.
- Distributed Ledger: The blockchain ledger is distributed across multiple nodes or participants. Each node maintains a copy of the entire blockchain. For any change to be accepted, a consensus must be reached among the majority of nodes. This distributed nature makes it extremely difficult for any single entity to alter the data.
The Role of Encryption in Peer-to-Peer Transactions
Blockchain operates in a decentralized environment, often referred to as peer-to-peer (P2P). In this setup, transactions occur directly between users without the need for intermediaries like banks or payment gateways.
- Decentralized Nature of Blockchain: Traditional systems rely on central authorities to validate and verify transactions. In contrast, blockchain operates on a network of distributed nodes that collectively validate transactions. This decentralization eliminates single points of failure and reduces vulnerabilities.
- How Encryption Ensures Trust in a Trustless Environment: In a P2P system, parties may not know or trust each other. Encryption bridges this trust gap. When a transaction is initiated, it’s encrypted using the sender’s private key and can only be decrypted by the recipient’s public key. This ensures that only the intended recipient can access the transaction details. Additionally, the transaction carries the digital signature of the sender, verifying its authenticity.
In the vast, interconnected world of blockchain, encryption stands as the guardian, ensuring that transactions are secure, authentic, and immutable. It’s the silent force that powers the trust and reliability blockchain promises, making it a transformative force in the digital landscape.
Threats and Challenges: The Importance of Strong Encryption
While blockchain boasts a robust security framework, it’s not entirely immune to threats. The evolving landscape of cyber threats necessitates continuous advancements in encryption techniques to stay ahead of potential vulnerabilities.
Potential Vulnerabilities in Blockchain
- 51% Attack: In blockchain networks that use Proof of Work (PoW) as a consensus mechanism, if a single miner or mining pool gains control of over 50% of the network’s computational power, they can potentially double-spend coins and prevent new transactions from gaining confirmations.
- Sybil Attack: In this attack, a single adversary controls multiple nodes on the network, undermining the decentralized nature of the system and potentially influencing consensus mechanisms.
- Eclipse Attack: Here, a node is isolated from the rest of the network and fed false information, potentially leading to double-spending or other malicious activities.
- Quantum Computing: The rise of quantum computers poses a potential threat to the cryptographic algorithms used in blockchain. Quantum computers can, in theory, break certain encryption methods faster than conventional computers.
The Ongoing Battle Against Quantum Computing
Quantum computers leverage the principles of quantum mechanics to process information at speeds unimaginable with today’s classical computers. While they hold promise for various fields, they also pose a significant threat to cryptographic systems, including blockchain.
- Post-Quantum Cryptography: Researchers are actively exploring cryptographic algorithms that can withstand quantum attacks. These algorithms, once standardized and tested, could replace current encryption methods, ensuring blockchain’s security in a post-quantum world.
Real-world Applications: Encryption in Action
Blockchain’s secure and transparent nature, powered by advanced encryption, has led to its adoption across various industries.
- Supply Chain Management: Blockchain ensures product authenticity and traceability throughout the supply chain, from raw materials to the end consumer. Encryption guarantees the integrity of data at every step.
- Healthcare: Patient records, treatment histories, and other sensitive data can be stored on the blockchain, ensuring data privacy and accessibility only to authorized personnel.
- Finance: Beyond cryptocurrencies, blockchain is revolutionizing traditional banking and financial systems by offering secure, transparent, and efficient transaction methods.
- Real Estate: Property titles, transaction histories, and other relevant data can be stored on the blockchain, reducing fraud and ensuring transparent property transfers.
- Voting Systems: Blockchain can be used to create tamper-proof voting systems where each vote is encrypted and securely stored, ensuring transparent and fraud-free elections.
The myriad applications of blockchain across industries underscore its transformative potential, with encryption at its core, ensuring data security, authenticity, and trustworthiness. As we continue to explore and harness the capabilities of blockchain, the role of encryption remains pivotal in shaping a secure and transparent digital future.
The Evolution of Encryption in Blockchain
The journey of encryption within the realm of blockchain is a testament to the ever-evolving nature of technology. As blockchain has matured, so have the cryptographic techniques that underpin it, ensuring that the system remains resilient against emerging threats.
Historical Perspective on Encryption Methods
- Symmetric Encryption: In the early days of digital encryption, symmetric encryption was prevalent. It involved a single key for both encryption and decryption. While simpler, it posed challenges, especially in a distributed system like blockchain, where sharing a single key among multiple parties could be a security risk.
- Asymmetric Encryption: This method, which uses a pair of public and private keys, became the foundation for blockchain encryption. It allowed for secure transactions in a decentralized environment, with the public key being used for encryption and the private key for decryption.
Innovations and Advancements in Cryptographic Techniques
- Zero-Knowledge Proofs: This cryptographic method allows one party to prove to another that a statement is true without revealing any specific information about the statement itself. In blockchain, this can be used to verify transactions without revealing transaction details, enhancing privacy.
- Multi-Signature Wallets: In the context of cryptocurrencies, multi-signature wallets require multiple private keys to authorize a transaction. This adds an extra layer of security, ensuring that even if one key is compromised, the funds remain safe.
- Homomorphic Encryption: A promising area of research, homomorphic encryption allows computations on ciphertexts, generating an encrypted result that, when decrypted, matches the result of the operations as if they had been performed on the plaintext. This has potential applications in privacy-preserving computations on blockchain.
The Intersection of Privacy and Security
Blockchain, by design, offers a high degree of transparency. Every transaction is recorded on a public ledger, accessible to anyone. However, this transparency can sometimes be at odds with the need for privacy.
- Public vs. Private Blockchains: While public blockchains are open and transparent, private blockchains restrict access and visibility. Private blockchains are often used by businesses and organizations that require privacy and control over their data.
- Privacy Coins: In the cryptocurrency world, privacy coins like Monero and Zcash have emerged, which prioritize user anonymity. They employ advanced cryptographic techniques to ensure that transaction details (sender, receiver, amount) are hidden.
- Layered Solutions: Technologies like the Lightning Network for Bitcoin aim to provide scalability and privacy by creating off-chain transaction channels. These solutions ensure faster transactions while keeping the details off the main blockchain, preserving user privacy.
Conclusion: The Future of Encryption in Blockchain
As we stand on the cusp of a new era in digital technology, the symbiotic relationship between blockchain and encryption becomes even more pronounced. The challenges posed by quantum computing, the need for greater privacy, and the ever-present threats from cyber-attacks will drive further innovations in cryptographic techniques.
Blockchain, with its promise of decentralized trust and transparency, combined with the robust security offered by advanced encryption, is set to play a pivotal role in shaping the digital landscape of the future. As industries and individuals increasingly adopt blockchain solutions, the continuous evolution and strengthening of encryption will be paramount in ensuring a secure, transparent, and efficient digital world.


Leave a Reply