
How to Protect Your Financial Data with SSL Certificates
In today’s digital age, the majority of our financial transactions, whether it’s checking bank balances, transferring funds, or even shopping online, occur over the internet. This convenience, however, comes with its own set of challenges, primarily concerning the security of the financial data being transmitted. As cyber threats continue to evolve and become more sophisticated, the need for robust security measures to protect sensitive financial information has never been more critical.
The Rise of Cyber Threats
Recent years have witnessed a surge in cyberattacks targeting financial institutions and individual users alike. From phishing scams that trick users into revealing their banking credentials to advanced malware designed to intercept and modify transactions, the array of threats is vast and ever-growing. A study by NSA predicts that by 2025, cybercrime damages will cost the world $10.5 trillion annually, with a significant portion targeting financial data.
Enter SSL/TLS: The Guardian of Online Transactions

Secure Socket Layer (SSL) and its successor, Transport Layer Security (TLS), are cryptographic protocols designed to ensure the security of data transmitted over the internet. At the heart of this security is the SSL certificate, a digital certificate that not only encrypts the data being sent and received but also verifies the identity of the website or platform you’re interacting with. In essence, it’s like a digital passport for websites, ensuring that the site you’re transacting with is genuine and that your data remains confidential and untampered.
| Term | Description |
|---|---|
| SSL (Secure Socket Layer) | An older security protocol developed in the 1990s to secure data transmission over the internet. |
| TLS (Transport Layer Security) | The successor to SSL, offering more robust and advanced security features. |
| SSL Certificate | A digital certificate that encrypts data and verifies the identity of a website. |
In the subsequent sections, we’ll delve deeper into the intricacies of SSL/TLS, exploring how they function, why they’re essential for financial data, and how you can ensure you’re benefiting from their protection.
Understanding SSL/TLS: The Backbone of Secure Online Transactions
The digital world is rife with potential threats, and as our reliance on online transactions grows, so does the importance of understanding the mechanisms that keep our data safe. At the forefront of these mechanisms are SSL and TLS.
What are SSL and TLS?
SSL, or Secure Socket Layer, was the original cryptographic protocol developed in the 1990s to secure data transmission over the Internet. Its primary function was to encrypt the data being sent between a user’s browser and a website’s server, ensuring that any intercepted data would be unreadable to unauthorized parties.
However, as technology advanced and cyber threats became more sophisticated, there was a need for a more robust security protocol. This led to the development of TLS, or Transport Layer Security, which is essentially an updated and more secure version of SSL. Today, while many still use the term “SSL” colloquially, most of the internet’s secure connections rely on TLS.
How Do They Work?
Both SSL and TLS operate by establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the server and browser remains private and integral.
The process begins with what’s known as an “SSL handshake.” During this handshake, the server and browser establish the terms of their communication:
- The browser requests a secure connection.
- The server responds with its SSL certificate.
- The browser verifies the certificate’s authenticity.
- Once verified, the browser sends back an encrypted key.
- The server decrypts this key using its private key, establishing an encrypted connection.
This entire process happens in mere seconds, yet it’s crucial for ensuring the security of the data being transmitted.
Evolution from SSL to TLS
While SSL laid the groundwork for online data security, its vulnerabilities became apparent as cyber threats evolved. TLS was introduced as a successor to address these vulnerabilities. Over the years, multiple versions of TLS have been released, with each iteration enhancing security features and addressing potential weaknesses.
| Version | Release Date | Improvements |
|---|---|---|
| SSL 2.0 | 1995 | Introduced basic encryption and authentication. |
| SSL 3.0 | 1996 | Improved upon 2.0 by fixing various vulnerabilities. |
| TLS 1.0 | 1999 | Addressed SSL 3.0 vulnerabilities and introduced new cryptographic algorithms. |
| TLS 1.1 | 2006 | Introduced protection against cipher block chaining attacks. |
| TLS 1.2 | 2008 | Added advanced cryptographic algorithms and removed insecure ones. |
| TLS 1.3 | 2018 | Simplified the protocol, improving security and speed. |
As we navigate the digital landscape, understanding the role and function of SSL and TLS is paramount. These protocols, while operating silently in the background, play a pivotal role in ensuring our financial data’s safety and integrity.
Why SSL Certificates Matter for Financial Data
Financial data, with its sensitive nature, is a prime target for cybercriminals. From credit card numbers to bank account details, the information we transmit online can have severe consequences if it falls into the wrong hands. This is where SSL certificates come into play, acting as a shield against potential threats.
Encryption: The First Line of Defense
At its core, an SSL certificate’s primary function is to encrypt data. When data is encrypted, it’s transformed into a code to prevent unauthorized access. Only the intended recipient, in possession of the correct decryption key, can revert it to its original form. This means that even if a hacker intercepts the data, without the decryption key, the information remains unreadable and useless.
Authenticity and Trustworthiness
Beyond encryption, SSL certificates serve another vital purpose: verification. When you visit a website, how can you be sure it’s genuine and not a cleverly disguised fraudulent site? The SSL certificate provides this assurance.
When a website has an SSL certificate, it’s undergone a verification process by a Certificate Authority (CA). The CA confirms the website’s legitimacy and its ownership. Once verified, the website is issued an SSL certificate, signaling to visitors that the site is genuine and trustworthy.
Data Integrity: Ensuring Unaltered Transmission
Data integrity is the assurance that the information hasn’t been altered during transmission. Without this guarantee, there’s a risk that the data sent from one party could be tampered with before reaching its destination. SSL certificates ensure that the data remains intact and unmodified, providing an additional layer of security.
Recognizing Secure Websites: The Padlock and HTTPS
For users, recognizing secure websites is straightforward. Sites with an active SSL certificate will display a padlock icon in the browser’s address bar. Additionally, the website’s URL will begin with “HTTPS” instead of the standard “HTTP.” The “S” stands for “secure,” indicating that the site has SSL protection.
The Cost of Ignoring SSL
For businesses, especially those dealing with financial transactions, not having an SSL certificate can have dire consequences. Beyond the obvious security risks, there’s a loss of customer trust. Modern browsers flag websites without SSL as “Not Secure,” deterring potential customers. Moreover, search engines prioritize secure sites, meaning non-SSL websites may suffer in search rankings.
SSL certificates are more than just a technicality; they’re a fundamental component of online financial security. They provide encryption, ensure data integrity, and verify website authenticity, collectively safeguarding both businesses and their customers from potential cyber threats.
The Process of SSL Handshake: Establishing a Secure Connection
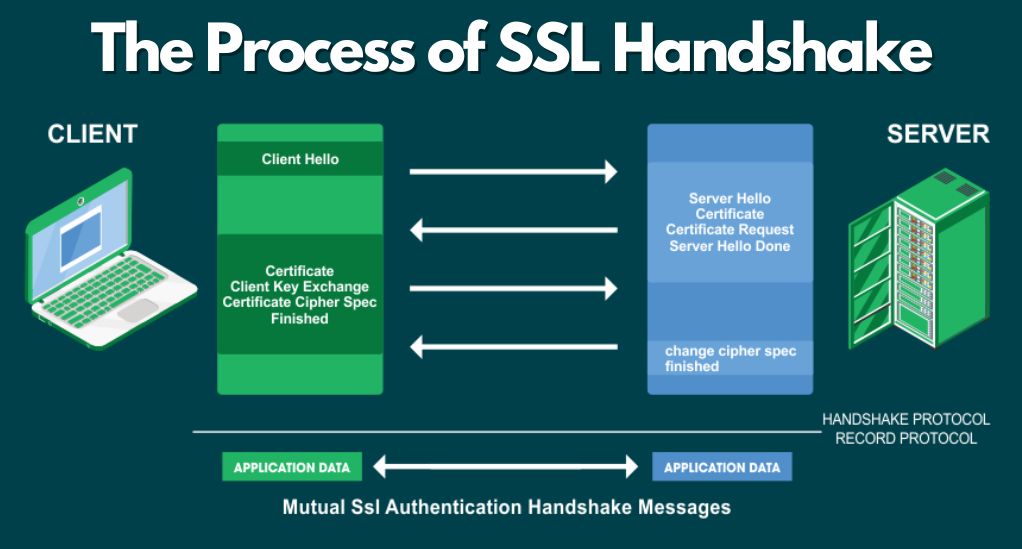
Every time we access a secure website or make an online transaction, a complex yet swift process unfolds behind the scenes to ensure our data’s safety. This process, known as the SSL handshake, is the foundation upon which secure online communication is built.
The Basics of the Handshake
The SSL handshake is a series of back-and-forth communications between a user’s browser (the client) and a website’s server. Its primary goal is to establish a secure connection using encryption, ensuring that the subsequent data transmission is both private and secure.
Step-by-Step Breakdown
- ClientHello: The process begins when the client sends a “ClientHello” message to the server. This message includes details like the SSL/TLS versions supported, a list of cryptographic algorithms (ciphers) the client supports, and a randomly generated value.
- ServerHello: The server responds with a “ServerHello” message, selecting the most appropriate SSL/TLS version and cipher based on the client’s list. The server also sends its own randomly generated value.
- Certificate Presentation: The server presents its SSL certificate to the client. This certificate contains the server’s public key and has been verified by a trusted Certificate Authority (CA).
- Certificate Verification: The client verifies the server’s certificate against a list of trusted CAs. If the certificate is valid and hasn’t expired, the process continues.
- Key Exchange: The client generates a pre-master secret, encrypts it with the server’s public key (from the certificate), and sends it to the server. Both the server and the client then use this pre-master secret to generate a session-specific symmetric encryption key.
- Finalization: Both parties exchange “Finished” messages, confirming that the handshake was successful and that a secure connection has been established.
Benefits of the SSL Handshake
- Dynamic Encryption: The encryption keys are session-specific, meaning they change with every session. This ensures that even if a cybercriminal intercepts the keys, they can’t use them for future sessions.
- Two-Way Authentication: While the server’s authentication is standard, clients can also be authenticated in certain high-security scenarios, ensuring both parties are genuine.
- Efficiency: Despite its complexity, the SSL handshake is incredibly efficient, completing within seconds and often going unnoticed by users.
Choosing the Right Certificate for Financial Transactions
Navigating the realm of SSL certificates can be daunting, especially given the array of options available. However, when it comes to financial transactions, the stakes are high, making it imperative to select the right certificate. This section delves into the different types of SSL certificates and offers guidance on choosing the most suitable one for financial platforms.
Types of SSL Certificates
- Domain Validated (DV) Certificates: These are the most basic type of SSL certificates. The Certificate Authority (CA) only verifies that the applicant has control over the domain for which the certificate is requested. While they provide encryption, they don’t validate the organization’s legitimacy, making them less ideal for financial platforms.
- Organization Validated (OV) Certificates: A step up from DV, OV certificates require the CA to validate the organization’s existence and its domain ownership. This provides a higher level of trust as users can be sure they’re interacting with a legitimate entity.
- Extended Validation (EV) Certificates: The gold standard for SSL certificates, EV certificates require a rigorous validation process. The CA verifies the organization’s legal, physical, and operational existence. Websites with EV certificates often display a green address bar or the company’s name in the address bar, instilling greater user confidence. For financial platforms, EV certificates are highly recommended.
- Wildcard Certificates: These certificates are useful for organizations with multiple subdomains. A single wildcard certificate can secure the main domain and an unlimited number of subdomains.
- Multi-Domain Certificates: As the name suggests, these certificates can secure multiple domain names with a single certificate, making them ideal for businesses operating multiple websites.
Factors to Consider When Choosing a Certificate
- Nature of the Platform: For platforms handling sensitive financial data, such as online banking or e-commerce sites, EV certificates are the best choice due to their rigorous validation process.
- Budget: While EV certificates offer the highest level of trust, they’re also more expensive. Organizations must balance their security needs with their budgetary constraints.
- Reputation of the Certificate Authority: Not all CAs are created equal. It’s crucial to choose a reputable CA known for its rigorous validation processes and robust security measures.
- Ease of Management: For organizations with multiple domains or subdomains, wildcard or multi-domain certificates can simplify certificate management.
- Warranty Level: Some SSL certificates come with warranties that compensate users if they suffer financial loss due to a faulty certificate. For financial platforms, considering the warranty level might be beneficial.
Implementing SSL for Financial Websites: Best Practices and Considerations
The decision to integrate SSL certificates into a financial platform is a commendable first step towards ensuring data security. However, the implementation process requires meticulous attention to detail and adherence to best practices. This section provides a roadmap for seamlessly integrating SSL certificates into financial platforms and highlights potential challenges and their solutions.
Steps to Integrate SSL Certificates
- Assessment and Planning: Before diving into the implementation, conduct a thorough assessment of the platform’s current security posture. Identify any existing vulnerabilities and determine the type of SSL certificate best suited for the platform.
- Select a Reputable Certificate Authority (CA): The choice of CA plays a pivotal role in the SSL certificate’s effectiveness. Opt for a well-known and trusted CA with a track record of rigorous validation processes.
- Generate a Certificate Signing Request (CSR): The CSR is a formal request to a CA for an SSL certificate. It contains details about the organization and the domain for which the certificate is requested.
- Install the Certificate: Once the CA validates the CSR and issues the SSL certificate, it needs to be installed on the server hosting the financial platform.
- Configure Server Settings: Optimize server settings to prioritize secure protocols like TLS 1.2 or TLS 1.3. Disable outdated protocols and ciphers to prevent potential vulnerabilities.
- Regularly Monitor and Renew: SSL certificates have an expiration date. Set up reminders to renew the certificate before it expires to avoid service interruptions.
- Implement HTTP Strict Transport Security (HSTS): HSTS is a security feature that ensures browsers only connect to the server using a secure HTTPS connection, preventing downgrade attacks.
Common Challenges and Solutions
- Expired Certificates: An expired certificate can lead to website downtime and loss of user trust. Implement automated reminders or use certificate management tools to track expiration dates.
- Misconfigurations: Incorrect server configurations can render the SSL certificate ineffective. Regularly audit server settings and use SSL testing tools to identify and rectify misconfigurations.
- Vulnerable Protocols and Ciphers: Outdated protocols and ciphers can be exploited by cybercriminals. Regularly update server configurations to disable vulnerable protocols and prioritize secure ones.
- Certificate Mismatch Errors: These errors occur when the domain name in the SSL certificate doesn’t match the domain name of the website. Ensure that the certificate accurately reflects the platform’s domain.
- Revoked Certificates: If a certificate is compromised, it may be revoked by the CA. Regularly check the certificate’s status and replace it if necessary.
In the ever-evolving landscape of cybersecurity, the implementation of SSL certificates for financial platforms is not a one-time task but an ongoing commitment. By adhering to best practices, regularly monitoring the platform’s security posture, and being proactive in addressing challenges, financial institutions can offer a secure and seamless experience to their users.
Future of Financial Data Security: Beyond SSL and TLS
While SSL and TLS have been the bedrock of online security for decades, the digital landscape is in a constant state of evolution. As technology advances and cyber threats become more sophisticated, the tools and protocols we rely on must also adapt. This section delves into the emerging trends and technologies that are set to shape the future of financial data security.
Quantum Computing and Post-Quantum Cryptography
Quantum computing, with its potential to process vast amounts of data at unprecedented speeds, poses both opportunities and challenges for cybersecurity. Traditional encryption methods, including some used in SSL/TLS, could become vulnerable to quantum attacks. In anticipation, researchers are developing post-quantum cryptographic algorithms designed to be resistant to quantum computing threats.
Blockchain and Financial Security
Blockchain, the technology underpinning cryptocurrencies like Bitcoin, offers promising applications for financial data security. Its decentralized and immutable nature ensures data integrity and transparency. Financial institutions are exploring blockchain for secure transactions, identity verification, and fraud prevention.
Machine Learning and AI in Cybersecurity
Machine learning and artificial intelligence (AI) are revolutionizing cybersecurity. By analyzing patterns and behaviors, AI can detect anomalies and potential threats in real-time, offering proactive security measures. For financial platforms, this means enhanced detection of fraudulent transactions or unauthorized access attempts.
Zero Trust Architecture
The traditional security model, often described as a “castle and moat,” relies on strong perimeter defenses. However, with the rise of cloud computing and remote work, this model is becoming obsolete. The Zero Trust architecture operates on the principle of “never trust, always verify.” Every access request, regardless of its origin, must be authenticated and authorized, ensuring granular security control.
Biometric Authentication
Passwords, while commonplace, have inherent vulnerabilities. Biometric authentication, using unique physical or behavioral attributes like fingerprints, facial recognition, or voice patterns, offers a more secure alternative. Financial platforms are increasingly integrating biometric authentication for enhanced user verification.
Continuous Authentication
Instead of a one-time login, continuous authentication monitors user behavior throughout a session. Any deviation from regular patterns, like rapid, high-value transactions, can trigger additional verification steps or alerts, ensuring ongoing security.
The Role of Regulation
As cyber threats evolve, so does the regulatory landscape. Governments and international bodies are introducing stricter data protection and cybersecurity regulations. Financial institutions must stay abreast of these changes, ensuring compliance while also leveraging them to enhance their security posture.
Conclusion
In the dynamic realm of cybersecurity, the emphasis has shifted from mere reactive measures to a proactive stance, where anticipation and continuous adaptation are paramount. Financial institutions, standing at the crossroads of technology and trust, must not only harness the latest advancements but also recognize the invaluable human element. Training, awareness, and a culture of security complement technological defenses, ensuring a holistic approach to safeguarding data.
Looking ahead, the challenges in financial data security will undoubtedly evolve, growing in both scale and complexity. Yet, with a commitment to continuous learning, collaboration, and innovation, these challenges can be met head-on. As we navigate this ever-changing landscape, the journey becomes as crucial as the destination, with each step reinforcing the pillars of trust and security in the digital financial world.


Leave a Reply