
How to Implement End-to-End Encryption in Messaging Apps
In today’s digital age, where communication has predominantly shifted to messaging apps, the importance of security and privacy in our conversations cannot be overstated. It’s here that End-to-End Encryption in Messaging Apps plays a pivotal role, ensuring our digital dialogues remain protected and confidential.
Below are step-by-step instructions on how to implement End-to-End Encryption (E2EE) in messaging apps, using WhatsApp and Telegram as examples. Please note that WhatsApp and Telegram already have E2EE implemented by default for all private conversations, but these steps can serve as a general guide for understanding how E2EE works in messaging apps.

- Download and Install WhatsApp: Ensure that you have the latest version of WhatsApp installed on your device.
- Verify Your Phone Number: Open WhatsApp and follow the prompts to verify your phone number.
- Start a New Chat: Tap on the chat icon in the bottom right corner and select a contact to start a new chat.
- Verify Encryption:
- Tap on the contact’s name at the top of the screen to open the contact info page.
- Scroll down and tap on “Encryption” to view the QR code and 60-digit number.
- If you are physically with the other person, you can scan each other’s QR code. Alternatively, you can compare the 60-digit number to verify that the chat is end-to-end encrypted.
- Send a Message: Type your message and hit send. Your message is now end-to-end encrypted.

Telegram
- Download and Install Telegram: Ensure that you have the latest version of Telegram installed on your device.
- Verify Your Phone Number: Open Telegram and follow the prompts to verify your phone number.
- Start a New Secret Chat:
- Tap on the pencil icon in the bottom right corner and select “New Secret Chat.”
- Choose a contact from your list to start a secret chat.
- Verify Encryption:
- Tap on the contact’s name at the top of the screen to open the contact info page.
- You will see a lock icon next to the contact’s name, indicating that the chat is end-to-end encrypted.
- You can also compare encryption keys in person to ensure the chat is secure.
- Send a Message: Type your message and hit send. Your message is now end-to-end encrypted.
Note
- In WhatsApp, all chats are end-to-end encrypted by default.
- In Telegram, you need to start a “Secret Chat” to enable end-to-end encryption as regular chats are not end-to-end encrypted by default.
- Always ensure that your app is up to date to benefit from the latest security features and updates.
By following these steps, you can ensure that your conversations on WhatsApp and Telegram are end-to-end encrypted, providing a higher level of security and privacy.
Here are step-by-step instructions for enabling and verifying end-to-end encryption in Signal, Messages (Apple’s iMessage), Messenger (Facebook Messenger), and Viber.

Signal
Signal is known for its strong focus on privacy and security, with end-to-end encryption enabled by default for all communications.
- Download and Install Signal: Ensure you have the latest version of Signal installed on your device.
- Verify Your Phone Number: Open Signal and follow the prompts to verify your phone number.
- Start a New Chat: Tap on the pencil icon to start a new chat and select a contact.
- Send a Message: Type your message and hit send. All messages and calls on Signal are end-to-end encrypted by default.

Messages (Apple’s iMessage)
iMessage automatically uses end-to-end encryption for all messages between Apple devices.
- Enable iMessage: Go to Settings > Messages and toggle on iMessage.
- Start a New Chat: Open the Messages app and start a new chat with another Apple device user.
- Verify Encryption: Look for the blue bubble; this indicates that the message is being sent via iMessage and is end-to-end encrypted. (Green bubbles indicate SMS messages, which are not end-to-end encrypted.)
- Send a Message: Type your message and hit send.

Messenger (Facebook Messenger)
Facebook Messenger offers end-to-end encryption in secret conversations.
- Download and Install Messenger: Ensure you have the latest version of Messenger installed on your device.
- Start a New Secret Conversation: Tap on your profile picture > Secret Conversations > Turn On.
- Choose a Contact: Go back to your chat list, tap on the pencil icon, and select “Secret” at the top right. Choose a contact to start a secret conversation.
- Verify Encryption: Tap on the contact’s name at the top of the screen to open the contact info page. You can verify the encryption key here.
- Send a Message: Type your message and hit send. Your message is now end-to-end encrypted.

Viber
Viber also provides end-to-end encryption by default for all one-on-one conversations, group chats, and calls.
- Download and Install Viber: Ensure you have the latest version of Viber installed on your device.
- Verify Your Phone Number: Open Viber and follow the prompts to verify your phone number.
- Start a New Chat: Select a contact to start a new chat.
- Verify Encryption: Look for a padlock icon in the chat header, indicating that the chat is end-to-end encrypted.
- Send a Message: Type your message and hit send.
By following these steps, you can ensure that your conversations on these messaging apps are end-to-end encrypted, providing a secure and private means of communication.
What is End-to-End Encryption (E2EE)?
End-to-End Encryption, often abbreviated as E2EE, is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation.
| Term | Description |
|---|---|
| E2EE | A system where only the communicating parties can access and read the messages. |
| Cryptographic Keys | Unique pieces of information that control the encryption and decryption of messages. |
| Eavesdropper | An unauthorized entity that tries to listen to a conversation, aiming to gain information illicitly. |
Why is E2EE Important?
The significance of E2EE lies in its ability to ensure that no one, other than the intended recipient, can access and read the message. This means that even if a hacker intercepts the message, they won’t be able to decipher its content without the unique cryptographic keys.
Imagine sending a sealed letter through the mail. While the postal service handles the letter, they can’t see its content because it’s sealed. Similarly, with E2EE, the service provider might transmit the message, but they can’t read it.
How Does E2EE Ensure Private Communication?
E2EE works by encrypting the message on the sender’s side and only decrypting it on the recipient’s side. The service providers in between – be it messaging apps, email services, or others – only see the encrypted version of the message. This ensures that even if the message is intercepted during transmission, it remains unreadable to unauthorized entities.
The Evolution of E2EE in Messaging
The concept of encryption is not new. It dates back to ancient civilizations where rulers and military leaders used coded messages to communicate secretly. However, the application of end-to-end encryption in digital messaging has evolved significantly over the years, adapting to the challenges and needs of the modern world.
Historical Context of Encryption
In ancient times, methods like the Caesar Cipher, where each letter in the plaintext was shifted a certain number of places down or up the alphabet, were used. Fast forward to World War II, and we see the use of the Enigma machine by the Germans, a more sophisticated encryption tool.
Modern Applications and Their Adoption of E2EE
As the digital era dawned, the need for more robust encryption methods became evident. With the rise of the internet and digital messaging platforms, the volume of personal and sensitive information being shared electronically skyrocketed.
- Instant Messaging Apps: Platforms like WhatsApp, Signal, and Telegram have integrated E2EE to ensure user conversations remain private. When you send a message on these platforms, it’s encrypted on your device and only decrypted on the recipient’s device.
- Email Services: Providers like ProtonMail offer E2EE for emails, ensuring that only the sender and recipient can access the content, keeping it hidden from email service providers and potential hackers.
- Video Conferencing Tools: With the rise of remote work and online meetings, tools like Zoom have started offering E2EE options to protect the privacy of their users during video calls.
| Modern Platform | E2EE Implementation |
|---|---|
| Uses the Signal Protocol to encrypt both one-on-one and group chats. | |
| ProtonMail | Encrypts emails such that even the service provider cannot access the content. |
| Zoom | Offers E2EE for video calls, ensuring that only the participants can view and hear the conversation. |
E2EE and Privacy Concerns
In an age where data breaches and cyber-attacks are becoming increasingly common, the need for secure communication has never been more paramount. While encryption plays a pivotal role in safeguarding our digital interactions, it’s essential to understand the nuances of different encryption methods and the privacy concerns associated with them.
The Difference Between Encryption ‘In Transit’ and End-to-End Encryption
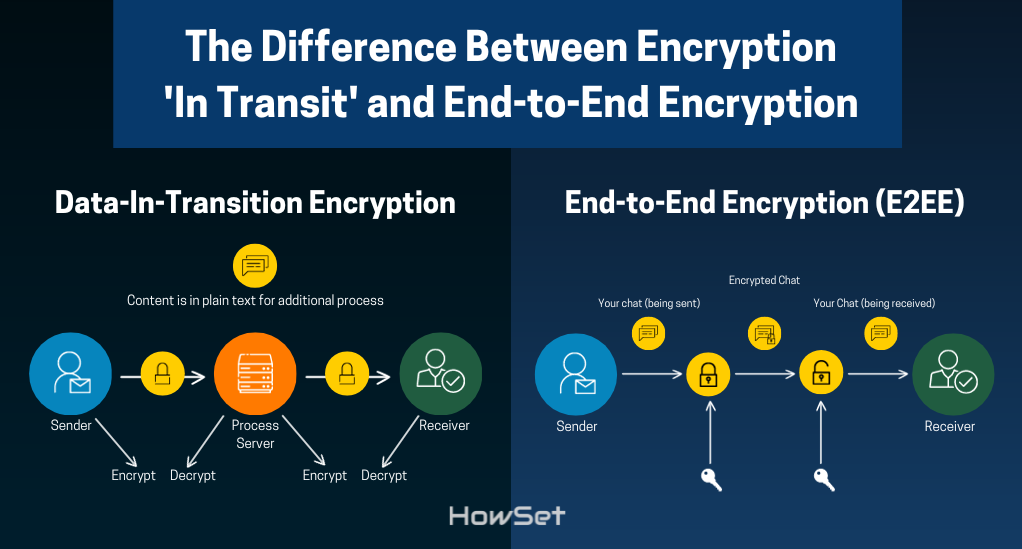
We can broadly categorize encryption into two types based on where the encryption and decryption take place:
- Encryption ‘In Transit’: This method encrypts data while it moves from sender to receiver. Yet, decryption can happen at intermediary points like servers before the data reaches its final destination. As a result, service providers or potential hackers with server access might read the data.
- End-to-End Encryption (E2EE): In E2EE, the sender encrypts data at the source, and only the receiver at the final destination decrypts it. No intermediary, not even the service provider, can decrypt the data along the way.
Risks Associated with Third-Party Intermediaries
When data is not end-to-end encrypted, it’s vulnerable to various risks:
- Service Provider Access: Without E2EE, service providers can access, read, and potentially misuse user data. This poses a significant privacy concern, especially if the provider’s intentions are not transparent.
- Data Breaches: When malicious entities compromise a service provider’s server, they can access any data stored on or passing through that server.
- Government Surveillance: In some regions, governments can legally request access to user data from service providers. Without E2EE, this data can be handed over, compromising user privacy.
The Imperative for E2EE in Modern Communication
Given the risks associated with non-E2EE methods, the shift towards end-to-end encrypted communication platforms is not just a trend but a necessity. Users are becoming increasingly aware of their digital rights and the importance of privacy. As a result, platforms that prioritize E2EE are gaining traction, as they offer a safer environment for digital interactions.
Challenges in Implementing E2EE
While End-to-End Encryption (E2EE) offers a robust layer of security for digital communications, its implementation is not without challenges. From technical hurdles to potential vulnerabilities, understanding these challenges is crucial for both developers and users.
Man-in-the-Middle (MITM) Attacks and Their Implications
One of the most significant threats to E2EE is the Man-in-the-Middle (MITM) attack. In this type of attack, a malicious actor intercepts the communication between two parties, potentially altering the messages without either party realizing.
For instance, during the initial key exchange process in E2EE, if a hacker can intercept the keys and replace them with their own, they can decrypt, read, and modify any messages sent between the two parties.
The Importance of Authentication in Preventing MITM Attacks
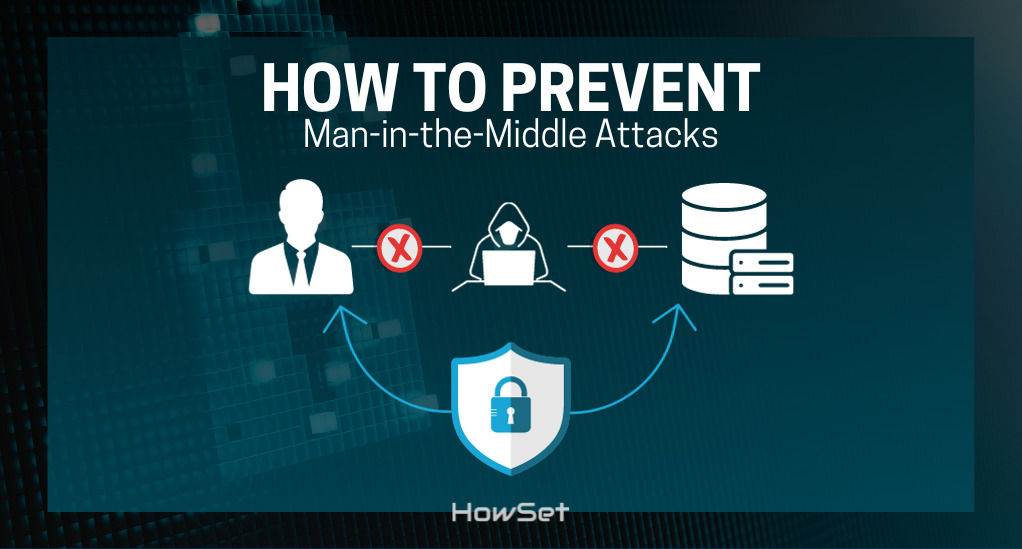
To counter MITM attacks, authentication becomes paramount. Authentication ensures that the parties involved in the communication are who they claim to be. Several methods can be employed:
- Public Key Pinning: This involves associating a host with their expected public key. If the key changes unexpectedly, it’s a sign of a potential MITM attack.
- Out-of-Band Verification: This method requires users to verify encryption keys through a separate channel. For instance, messaging apps might use QR codes that users can scan in person to verify each other’s identities.
- Certificate Authorities (CAs): Trusted organizations can issue digital certificates that verify the owner’s identity and the public key’s validity.
Technical Complexities in E2EE Implementation
Implementing E2EE is not just about countering potential attacks. There are inherent technical challenges:
- Key Management: Securely generating, distributing, storing, and disposing of encryption keys is a complex task. If keys are mishandled or lost, it can lead to data being permanently inaccessible.
- Performance Overhead: Encryption and decryption processes can introduce latency, especially in real-time communications like video calls.
- Cross-Platform Compatibility: Ensuring E2EE works seamlessly across different devices, operating systems, and application versions can be challenging.
Endpoint Security in E2EE
While End-to-End Encryption (E2EE) ensures that data remains encrypted and secure during transmission, the security of the endpoints—the devices where encryption and decryption occur—becomes equally vital. If an endpoint is compromised, the benefits of E2EE can be negated.
Risks at the Communication Endpoints
The strength of E2EE lies in ensuring that data remains unreadable during transit. However, before encryption and after decryption, the data is in its readable form at the endpoints. This presents potential vulnerabilities:
- Device Malware: Malware, particularly keyloggers or screen recorders, on a device can capture sensitive information either before encryption or after decryption.
- Physical Device Access: If someone gains unauthorized physical access to a device, especially one without a password or with a simple password, it risks a data breach.
- Outdated Software: Devices running outdated software or operating systems may expose known vulnerabilities that attackers can exploit.
Measures to Increase Endpoint Security
To ensure the effectiveness of E2EE, the security of the endpoints must be fortified:
- Regular Software Updates: Update the device’s software and applications regularly to patch known vulnerabilities.
- Multi-Factor Authentication (MFA): Implementing MFA adds an additional layer of security, making unauthorized access more challenging.
- Device Encryption: Encrypt the device’s storage to keep data secure, even if someone loses or steals the device.
- Anti-Malware Software: Scan devices for malware regularly and keep anti-malware software updated to ward off data breaches.
- Educating Users: Often, the weakest link in security is human behavior. Educating users about the importance of strong, unique passwords and recognizing phishing attempts can significantly enhance endpoint security.
The Controversy Surrounding Backdoors
End-to-End Encryption (E2EE) stands as a cornerstone of digital privacy, ensuring the confidentiality of our online communications. However, its widespread adoption has ignited debates and controversies, especially concerning the concept of “backdoors.”
Definition and Implications of Backdoors
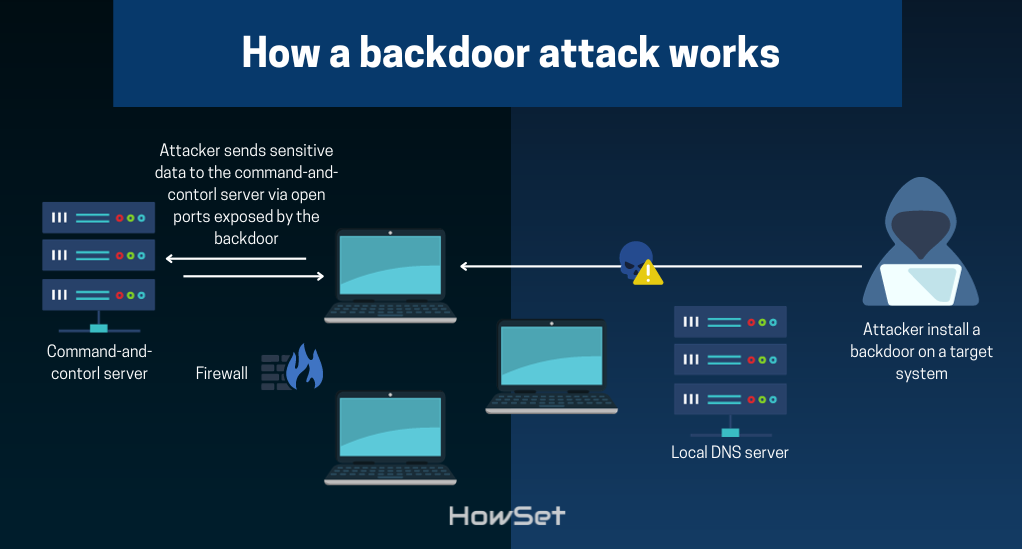
A “backdoor” in the context of encryption refers to a method by which authorized entities, such as governments or law enforcement agencies, can bypass encryption mechanisms to access the content of encrypted communications. While the intention behind backdoors is often to combat criminal activities or threats to national security, their existence poses significant challenges:
- Privacy Concerns: The very essence of E2EE is to provide users with a guarantee of privacy. Introducing backdoors compromises this guarantee, leading to potential misuse and surveillance.
- Security Risks: Backdoors, even if intended for legitimate use, can be exploited by malicious actors. Once a backdoor exists, it becomes a potential vulnerability that hackers can target.
- Trust Issues: Knowing that a platform has a backdoor can erode trust among its users, leading them to seek alternative platforms or methods of communication.
Historical Instances of Backdoor Controversies
The debate surrounding backdoors isn’t new. Several historical instances highlight the tension between privacy advocates and authorities:
- Apple vs. FBI (2016): The FBI sought Apple’s assistance in unlocking an iPhone belonging to a perpetrator of a terrorist attack. Apple resisted, citing concerns over creating a backdoor that could be misused in the future.
- Encryption Wars of the 1990s: The U.S. government proposed the “Clipper Chip,” an encryption device with a built-in backdoor for government access. The proposal was met with significant opposition and was eventually abandoned.
Balancing National Security and Individual Privacy
The crux of the backdoor controversy lies in balancing the needs of national security with the rights of individual privacy. While there’s no easy solution, a few potential approaches have been suggested:
- Transparent Oversight: Strict oversight must govern any backdoor access, ensuring use only in justified situations.
- Time-Limited Access: Rather than using permanent backdoors, consider implementing access mechanisms with a set expiration period.
- User Consent: Platforms could offer users the choice to opt-in or opt-out of potential backdoor access, giving them control over their data.
Balancing E2EE with Compliance and Regulatory Requirements
End-to-End Encryption (E2EE) stands as a bastion of digital privacy, but its widespread implementation brings it into direct conflict with various compliance and regulatory requirements. Organizations, especially those operating in regulated industries, often find themselves navigating the tightrope between ensuring user privacy and adhering to legal mandates.
The Need for Content Inspection in Businesses
Many businesses and industries have legitimate reasons to inspect content:
- Data Loss Prevention (DLP): Organizations monitor and control data transfers to stop leaks or inappropriate sharing of sensitive information.
- Archiving for Compliance: Law mandates certain sectors, such as finance and healthcare, to keep communication records for set durations.
- Monitoring for Malicious Content: To protect against malware and phishing attacks, businesses often need to inspect content in real-time.
While E2EE ensures data privacy, it can also obstruct these essential business functions by making content inspection challenging.
How Organizations Navigate E2EE and Regulatory Mandates
Given the conflicting demands of E2EE and compliance, organizations employ various strategies:
- Selective Encryption: Not all data might be subject to the same level of sensitivity. Organizations can choose to apply E2EE only to the most sensitive data, leaving other data encrypted in transit but available for inspection when necessary.
- Managed Access: Systems securely manage decryption keys, allowing access only under specific conditions. This approach ensures compliance requirements can decrypt data while still protecting it from unauthorized access.
- Clear Communication with Users: It’s crucial to communicate transparently with users about data access times and reasons. Clear privacy policies and user agreements achieve this transparency.
The Global Landscape of E2EE Regulations
Different countries have varying stances on E2EE, influenced by their cultural, political, and security contexts:
- Pro-E2EE Regulations: Some regions, valuing individual privacy, have strong protections in place for encrypted communications, resisting attempts to mandate backdoors.
- Anti-E2EE Regulations: Other regions, prioritizing national security or law enforcement capabilities, have sought to limit the use of E2EE or mandate backdoors.
- Balanced Approach: Some countries are attempting to strike a balance, allowing E2EE but with provisions for legal access under specific circumstances.
Conclusion: The Future of E2EE in Messaging Apps
The rise of End-to-End Encryption (E2EE) in messaging apps signifies a pivotal shift towards prioritizing digital privacy in our interconnected age. Driven by user demand, technological advancements, and global events highlighting the need for secure communication, E2EE has become a cornerstone of modern digital dialogue. However, as we look ahead, challenges such as the advent of quantum computing, regulatory pushback, and the continuous evolution of technology loom large. Balancing these challenges with the unwavering commitment to user privacy will shape the future trajectory of E2EE, emphasizing the importance of user education, regular updates, and transparent, open-source solutions.


Leave a Reply