How to Master Advanced Encryption Algorithms: AES vs. RSA
In an increasingly digital world, the security of our data and communications has become paramount. Encryption plays a pivotal role in safeguarding sensitive information from prying eyes and malicious actors. Understanding advanced encryption algorithms is crucial for individuals, businesses, and organizations alike as they seek to protect their digital assets. In this article, we will delve into the intricacies of two prominent encryption algorithms: AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman).
Overview of Encryption Algorithms
Before diving into the specifics of AES and RSA, it’s essential to grasp the fundamental concept of encryption algorithms. At its core, encryption is the process of converting plaintext data into ciphertext, rendering it unreadable without the corresponding decryption key. This transformation is achieved through complex mathematical algorithms designed to withstand various attacks.
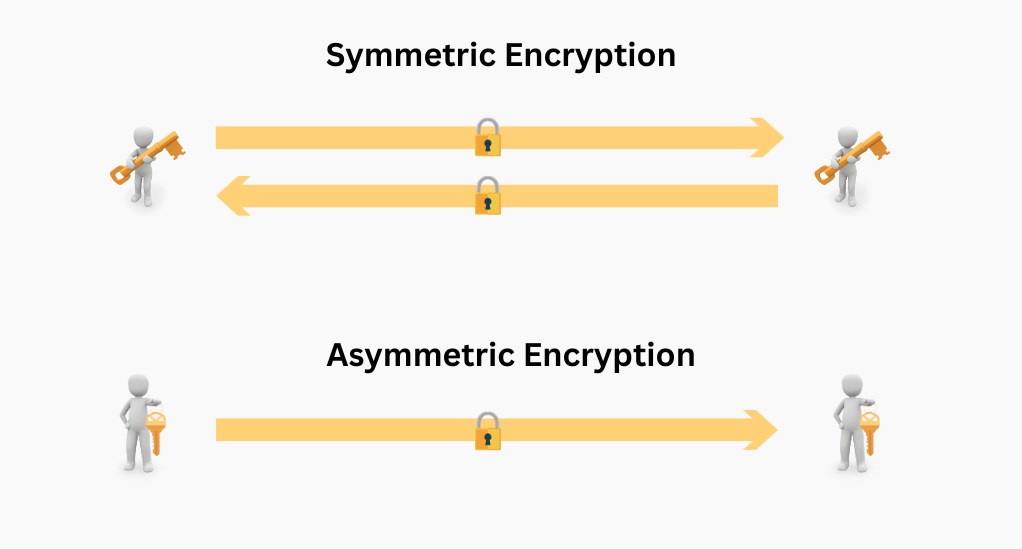
Encryption algorithms fall into two categories: symmetric-key encryption and asymmetric-key encryption. Each category serves different purposes and has its strengths and weaknesses.
- Symmetric-Key Encryption: In symmetric-key encryption, a single secret key is used for both encryption and decryption. It’s like having one key to lock and unlock a safe. This approach is efficient and fast, making it suitable for encrypting large amounts of data. AES is a prime example of a symmetric-key encryption algorithm.
- Asymmetric-Key Encryption: Asymmetric-key encryption employs a pair of keys – a public key for encryption and a private key for decryption. It’s like having one key to lock and another unique key to unlock. RSA is a widely used asymmetric-key encryption algorithm.
To illustrate the difference between these two types of encryption, consider the following table:
| Aspect | Symmetric-Key Encryption (AES) | Asymmetric-Key Encryption (RSA) |
|---|---|---|
| Number of Keys | One | Two (public and private) |
| Key Distribution | More challenging | Easier (public key can be shared) |
| Speed and Efficiency | Faster | Slower |
| Use Cases | Data encryption at rest | Digital signatures, key exchange |
| Security | Sensitive to key distribution | More secure for key exchange |
Understanding AES (Advanced Encryption Standard)
AES, or Advanced Encryption Standard, represents the gold standard in symmetric-key encryption. It is the go-to encryption algorithm for securing data at rest and in transit, offering a robust and efficient method for safeguarding information. To master AES, one must delve into its history, workings, strengths, and weaknesses.
History and Development of AES
The need for a more secure and standardized encryption algorithm became evident as older algorithms like DES (Data Encryption Standard) began to show vulnerabilities in the face of evolving cyber threats. In response, the U.S. National Institute of Standards and Technology (NIST) initiated a competition in 1997 to develop a new encryption standard that would be both secure and efficient.
After a rigorous evaluation process, Rijndael, a symmetric-key encryption algorithm developed by Belgian cryptographers Vincent Rijmen and Joan Daemen, emerged as the winner in 2001. It was subsequently adopted as the Advanced Encryption Standard, cementing its place as the de facto symmetric-key encryption algorithm.
How AES Works
AES operates through a series of substitution, permutation, and mixing operations, known as rounds. It encrypts data blocks of fixed sizes (128, 192, or 256 bits) and employs a secret key for encryption and decryption. The key size corresponds to the level of security, with longer keys providing greater protection.
The key operations in AES are as follows:
- SubBytes: Byte-level substitution using an S-box (substitution box).
- ShiftRows: Shifting the rows of the data matrix.
- MixColumns: Mixing data within columns.
- AddRoundKey: Applying a round-specific subkey derived from the main encryption key.
This process repeats for a specified number of rounds, depending on the key size (10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys). After the final round, the ciphertext is generated.
Strengths and Weaknesses of AES
AES exhibits numerous strengths that have led to its widespread adoption. Firstly, it is highly regarded for its security, having withstood rigorous cryptanalysis, especially when employed with adequate key lengths. Second, AES is exceptionally efficient in terms of computation, rendering it ideal for real-time data encryption. Third, its status as an international standard ensures compatibility across diverse platforms and systems. Lastly, AES’s versatility shines through as it can be implemented across various hardware and software environments, even on resource-constrained devices.
Nevertheless, AES is not without its limitations. Chiefly, effective key management is imperative for maintaining its security, which can pose challenges, particularly when it comes to secure key distribution and storage.
Moreover, while quantum vulnerability is not an immediate concern, the potential for future quantum computers with sufficient computing power to compromise AES security looms as a consideration for long-term data protection strategies.
Demystifying RSA (Rivest-Shamir-Adleman)

RSA, named after its creators Ron Rivest, Adi Shamir, and Leonard Adleman, is a prominent asymmetric-key encryption algorithm known for its role in securing digital communication and data integrity. To master RSA, we need to delve into its origins, mathematical principles, use cases, and limitations.
The Origins and Creators of RSA
RSA encryption was introduced in 1977 when the three inventors published their groundbreaking paper outlining the algorithm’s principles. The trio’s pioneering work revolutionized cryptography by introducing the concept of public-key cryptography, which enabled secure communication between parties who had never met before.
RSA’s Mathematical Principles
At the heart of RSA encryption are two mathematically linked keys: a public key and a private key.
- Public Key: This key is used for encryption and is freely shared with anyone who wants to send you secure messages. It is derived from the product of two large prime numbers, making it computationally infeasible to factorize and discover the private key.
- Private Key: The private key, on the other hand, is kept secret and used for decryption. It is based on the factors of the product of the two prime numbers from which the public key was derived.
The security of RSA relies on the difficulty of factoring the product of two large prime numbers, even with the most powerful computers. This mathematical challenge forms the basis of RSA’s strength.
Use Cases and Limitations of RSA
RSA serves a diverse array of purposes in the realm of cybersecurity. It finds application in ensuring secure communication, including emails, online banking transactions, and e-commerce activities. Additionally, RSA’s digital signature capabilities are instrumental in verifying the authenticity and integrity of various digital documents and messages. Moreover, RSA plays a pivotal role in facilitating secure key exchange between parties, allowing them to establish a shared secret key for use in symmetric-key encryption.
However, it’s important to acknowledge certain limitations associated with RSA encryption. The security of RSA is intricately tied to the length of the keys employed. As computing power advances, longer keys become necessary to uphold the desired level of security, rendering key length selection a crucial consideration.
Furthermore, RSA encryption and decryption operations can be computationally demanding, particularly when dealing with longer key lengths. Lastly, the advent of quantum computing poses a looming threat to RSA encryption, much like AES, necessitating the exploration and adoption of post-quantum cryptography solutions to preserve the integrity of data security.
AES vs. RSA: A Comparative Analysis
Now that we have explored the fundamentals of both AES and RSA encryption algorithms, it’s time to delve into a detailed comparative analysis. Understanding the differences between these two cryptographic approaches is pivotal in making informed decisions about when and how to use them effectively.
Key Differences Between AES and RSA
- Key Type:
- AES: Uses a single secret key for both encryption and decryption, known as symmetric-key encryption.
- RSA: Employs a pair of keys—a public key for encryption and a private key for decryption, known as asymmetric-key encryption.
- Speed and Efficiency:
- AES: Known for its efficiency and speed, making it suitable for encrypting large volumes of data in real-time.
- RSA: Generally slower due to the complexity of asymmetric encryption operations, making it less suitable for high-speed data encryption.
- Use Cases:
- AES: Primarily used for data encryption at rest, securing data on storage devices and during transmission.
- RSA: Used for digital signatures, key exchange, and securing communication over untrusted networks.
- Key Management:
- AES: Requires efficient key management, particularly for securely distributing and storing secret keys.
- RSA: Offers more straightforward key distribution as the public key can be openly shared, but private key protection is crucial.
- Security:
- AES: Highly secure when implemented with appropriate key lengths and good key management practices.
- RSA: Also secure when using sufficiently long key lengths, but quantum computing poses a potential threat.
- Performance:
- AES: Exceptional performance in terms of encryption and decryption speed.
- RSA: Slower performance due to the computational complexity of asymmetric encryption.
When to Use AES or RSA
The choice between AES and RSA hinges on the specific use case and security requirements. AES is often preferred for data encryption tasks such as securing files, databases, or data in transit due to its speed and efficiency. In contrast, RSA’s asymmetric encryption capabilities make it invaluable for ensuring secure communication over the internet and safeguarding sensitive data during transmission.
RSA excels in generating digital signatures, which serve as guarantees of document and message authenticity. Its capacity to facilitate secure key exchange also makes RSA an ideal choice for establishing shared secrets, which can subsequently be employed alongside AES for robust and secure communication.
Moreover, with the looming threat of quantum computing, adopting quantum-resistant cryptographic methods is becoming imperative, particularly when addressing long-term data security concerns.
Mastering AES Encryption
Now that we’ve examined the differences and use cases for AES and RSA, let’s focus on mastering AES encryption, the cornerstone of symmetric-key cryptography. By gaining expertise in AES, you’ll be better prepared to secure your data efficiently and effectively.
Practical Tips for Implementing AES
- Choose the Right Key Length: The security of AES depends on the length of the encryption key. Longer keys offer greater security but require more computational resources. Assess your security needs and select an appropriate key length, such as 128, 192, or 256 bits.
- Implement Proper Key Management: Securely managing encryption keys is crucial. Use established key management practices to protect keys from unauthorized access. Consider employing hardware security modules (HSMs) for added protection.
- Use Industry-Standard Tools: Utilize reputable encryption software and libraries that implement AES correctly. Well-known cryptographic libraries like OpenSSL or libraries provided by cloud service providers are good choices.
- Regularly Update Keys: Periodically update encryption keys to minimize the risk of a successful attack. Key rotation and proper archival of old keys are essential.
- Data Segmentation: Consider segmenting your data and applying different encryption keys to different data sets or files. This practice limits the impact of a potential breach.
Best Practices for AES Key Management
Effective key management is vital for AES encryption. Here are some best practices to follow:
- Generate Strong Random Keys: Use cryptographically secure random number generators to create encryption keys. Weak or predictable keys can compromise security.
- Secure Key Storage: Store encryption keys in secure, isolated environments. Hardware security modules (HSMs) or key vaults offered by cloud providers provide a robust solution for key storage.
- Key Backup and Recovery: Establish backup and recovery procedures for encryption keys to prevent data loss in case of key loss or corruption.
- Access Controls: Implement strict access controls to ensure only authorized personnel can access encryption keys and related systems.
- Key Destruction: When keys are no longer needed, ensure they are properly destroyed to prevent unauthorized decryption of data.
By adhering to these best practices, you can master AES encryption and use it effectively to protect your data at rest and during transmission.
Mastering RSA Encryption
RSA encryption, with its unique properties and applications, is a crucial component of modern cryptography. To master RSA, you need to understand how to implement it effectively and securely.
Practical Tips for Implementing RSA
- Generate Strong Key Pairs: Begin by generating a strong RSA key pair with a sufficiently large modulus. Longer key lengths, such as 2048 or 3072 bits, enhance security. Tools like OpenSSL or libraries in various programming languages can help generate key pairs.
- Key Storage and Protection: Safeguard your private key, as it is critical for decryption. Store it securely in a tamper-resistant hardware security module (HSM) or an offline device. Regularly back up your private key and keep it in a secure, offsite location.
- Secure Key Exchange: When using RSA for key exchange, ensure the public keys are exchanged securely. Techniques like key pinning and certificate validation can prevent man-in-the-middle attacks.
- Digital Signatures: If implementing RSA for digital signatures, follow best practices for signature generation and verification. Keep your private key safe to prevent unauthorized signing.
- Consider Forward Secrecy: In situations where long-term security is a concern, consider implementing forward secrecy using protocols like Diffie-Hellman (Ephemeral or Elliptic Curve) in conjunction with RSA.
Best Practices for RSA Key Management
Effective RSA key management is crucial for maintaining the security of your cryptographic operations:
- Regular Key Rotation: Periodically change your RSA key pairs to mitigate the risk of long-term key compromise. Implement a key rotation schedule.
- Key Archiving: Properly archive old keys for potential decryption of historical data. Ensure these archives are secure and well-documented.
- Access Controls: Restrict access to private keys to authorized personnel only. Use access controls and audit logs to monitor key usage.
- Key Destruction: When you no longer require RSA keys, securely destroy them to prevent unauthorized decryption.
- Stay Informed: Keep up-to-date with cryptographic best practices and vulnerabilities related to RSA encryption. Regularly review and update your cryptographic implementations.
By mastering RSA encryption and adhering to these best practices, you can confidently use RSA for securing communication, digital signatures, and key exchange.
Enhanced Cybersecurity with AES and RSA
In today’s digital age, where threats to data security are continually evolving, combining the strengths of AES and RSA encryption can provide a powerful strategy for enhanced cybersecurity. This section will explore how leveraging both encryption methods can bolster your defense against various security threats.
Combining AES and RSA for Stronger Encryption
One powerful approach to cybersecurity is to use AES for data encryption and RSA for key exchange and digital signatures. This hybrid approach leverages the strengths of both algorithms:
- Data Encryption with AES: Utilize AES to encrypt sensitive data at rest or during transmission. AES excels in providing efficient and fast encryption, making it ideal for securing large volumes of data.
- Key Exchange with RSA: Use RSA for secure key exchange. When two parties need to communicate securely, RSA’s public key can facilitate the exchange of a shared secret key for symmetric encryption (such as AES). This ensures that even if an adversary intercepts the communication, they won’t have access to the encryption keys.
- Digital Signatures with RSA: RSA’s digital signature capabilities can be employed to verify the authenticity and integrity of messages, documents, or software updates. By signing data with a private key, recipients can verify that the data hasn’t been tampered with during transit.
Protecting Data in Transit and at Rest
By implementing AES for data encryption, you enhance data security in two fundamental scenarios. Firstly, when data is in transit—transmitted over networks or the internet—encrypting it with AES ensures that even if intercepted, it remains indecipherable to unauthorized parties. Secondly, when data is at rest—stored on devices, servers, or in the cloud—AES encryption provides a robust defense, guarding against unauthorized access in the event of data breaches or physical theft. This dual protection ensures that sensitive information remains confidential, whether in motion or at rest.
Staying Ahead of Emerging Threats
In the ever-evolving cybersecurity landscape, new threats continuously emerge. Combining AES and RSA encryption methods offers a proactive strategy for staying ahead of these challenges.
One significant advantage is achieving Quantum-Resistant Security. As quantum computing technology progresses, RSA encryption may become vulnerable. By integrating AES and RSA, you can seamlessly transition to post-quantum cryptographic methods for key exchange while maintaining the robustness of AES for data encryption.
Furthermore, this approach enhances defense against Man-in-the-Middle Attacks. RSA key exchange plays a pivotal role in safeguarding communication channels, ensuring secure and trustworthy exchanges. Additionally, RSA’s digital signatures contribute to preserving data integrity by preventing unauthorized alterations. This amalgamation of encryption methods forms a comprehensive strategy for fortified cybersecurity in the face of evolving threats.
Conclusion: Becoming an Encryption Expert
In an increasingly digital and interconnected world, the mastery of encryption algorithms is not just a skill—it’s an imperative for safeguarding our data and communications. This article has provided a comprehensive roadmap to understanding and applying two of the most influential encryption methods: AES and RSA.
As you embark on your journey to become an encryption expert, remember that the power lies not only in knowing how these algorithms work but also in applying them effectively. Whether you’re securing data at rest or in transit, communicating securely, or ensuring the integrity of your digital signatures, the knowledge you’ve gained here equips you to navigate the evolving landscape of cybersecurity. Stay vigilant, stay informed, and continue to adapt, for in the realm of encryption, continuous learning is the key to staying ahead of emerging threats and challenges.


Leave a Reply