The Ultimate Guide to Password Management: Securing Your Digital Frontier
In the digital age, the significance of robust password management cannot be overstated. As we navigate through an ever-increasing online landscape, the necessity to safeguard our digital assets has become paramount. This comprehensive guide aims to equip you with the knowledge and tools to fortify your online presence effectively. Let’s delve step by step into the intricate world of password management.
The Importance of Password Management
In the contemporary digital ecosystem, an individual manages a plethora of online accounts, ranging from social media platforms to banking services. Each of these accounts contains sensitive personal data that could be exploited if fallen into the wrong hands. Here, password management acts as the first line of defense, safeguarding your digital identity from potential cyber threats.
Why is it Crucial?
Secure passwords serve as a cornerstone in safeguarding your digital life, acting as a formidable barrier against unauthorized access to personal data. They play a pivotal role in ensuring financial security, especially on platforms involving online banking and shopping, where a robust password system is indispensable.
Moreover, adept password management is a potent tool in preventing identity theft, thwarting cybercriminals from impersonating you and engaging in fraudulent activities. Through vigilant password practices, you can foster a secure and trustworthy digital environment.
Current Trends in Cybersecurity
As technology evolves, so does the sophistication of cyber threats. It’s imperative to stay abreast of the current trends in cybersecurity to build a resilient defense mechanism. Here, we explore some of the prevailing trends that are shaping the cybersecurity landscape.
- Rise in Phishing Attacks: Cybercriminals are increasingly using phishing attacks, where they impersonate trustworthy entities to lure individuals into providing sensitive information.
- Increase in Ransomware Attacks: There has been a noticeable surge in ransomware attacks, where hackers encrypt data and demand a ransom for its release.
- Adoption of Multi-factor Authentication (MFA): Many platforms are now adopting MFA to add an extra layer of security. It requires users to verify their identity using two or more different methods before granting access.
- AI and Machine Learning in Cybersecurity: The integration of AI and machine learning in cybersecurity tools is helping in predicting and mitigating potential threats more effectively.
Understanding Password Encryption
In the journey to fortify our digital lives, understanding and implementing password encryption stands as a pivotal step. This section will guide you through the nuances of password encryption, its importance, and the tools and techniques available to ensure a secure digital environment.
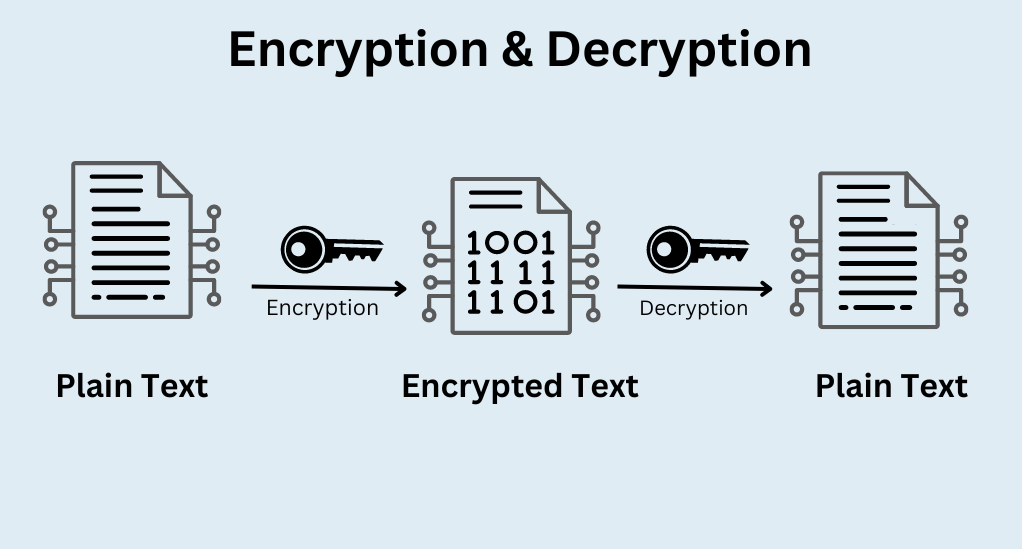
What is Password Encryption?
Password encryption is a security process where information is encoded and can only be accessed or decrypted by someone with the correct encryption key or password. This process is vital in safeguarding your data from unauthorized access. Let’s break down the concept further:
- Symmetric Encryption: In this type, the same key is used for both encryption and decryption. While it is faster, the key needs to be securely shared between the parties, which can be a vulnerability.
- Asymmetric Encryption: This involves a pair of keys – a public key (known to everyone) and a private key (known only to the recipient). It is more secure but slower compared to symmetric encryption.
How Does it Enhance Security?
Password encryption acts as a formidable barrier against potential cyber threats, significantly enhancing security in several ways. Firstly, it safeguards data during transmission, thwarting unauthorized access and ensuring the confidentiality of sensitive information, which remains accessible only to individuals possessing the correct decryption key.
Furthermore, encryption maintains the integrity of data by preventing alterations or tampering during transmission, thereby fostering a secure communication environment. Moreover, it authenticates the parties involved in the communication, guaranteeing that the data is exchanged with the intended recipient, thus fostering a secure and trustworthy digital communication landscape.
Tools and Techniques for Password Encryption
To implement password encryption effectively, various tools and techniques are available that offer a range of features to secure your digital assets. Here, we explore some popular options:
- Password Managers: These tools not only store your passwords securely but also offer features to encrypt passwords with robust algorithms.
- Virtual Private Networks (VPNs): VPNs encrypt your internet connection, securing the data transmission between your device and the server.
- Secure Sockets Layer (SSL): A standard technology for establishing an encrypted link between a server and a client, commonly used in web browsers for secure communications.
Secure Password Storage
As we further navigate the intricate pathways of password management, the next crucial stop is understanding secure password storage. This segment will elucidate the importance of safeguarding your passwords and the best practices and tools that can assist you in achieving this goal.
Importance of Secure Storage
In the digital domain, safeguarding passwords is equally crucial as formulating robust ones. Secure storage serves as a bulwark against unauthorized access, shielding your personal and financial details from prospective cyber threats.
This method is pivotal for several reasons: it acts as a fortress preventing data breaches that could culminate in financial and personal losses; it thwarts identity theft by barring cybercriminals from unauthorized access to your accounts; and it maintains privacy by ensuring the confidentiality of your personal information in the online arena.
Best Practices for Storing Passwords
To fortify your digital assets, adhering to the best practices for storing passwords is essential. Here, we outline some strategies that can be instrumental in achieving secure storage:
- Use of Password Managers: Utilize password managers that offer encrypted storage, making it nearly impossible for hackers to access your data.
- Regular Updates: Regularly update your passwords to minimize the risk of unauthorized access.
- Avoiding Common Passwords: Refrain from using common passwords that are easy to guess and crack.
- Two-Step Verification: Implement two-step verification wherever possible to add an additional layer of security.
Tools for Secure Password Storage
To ensure the secure storage of your passwords, several tools equipped with a myriad of features are readily available. Noteworthy options include password managers such as LastPass, Dashlane, and 1Password, which provide secure vaults for effective password management.
Additionally, you can enhance security through biometric authentication methods, including fingerprint or facial recognition. Moreover, encrypted digital notebooks serve as a reliable platform to securely store sensitive information, adding another layer to your digital safety net.
Multi-factor Authentication: A Must-Have in Today’s Digital Age
In our ongoing journey to master the art of password management, we now turn our focus towards multi-factor authentication (MFA), a security protocol that has become an essential component in safeguarding online identities. This section will guide you through the intricacies of MFA, illustrating how to set it up and why it is a vital tool in enhancing your online security.
Understanding Multi-factor Authentication
Multi-factor authentication is a security process that requires users to provide two or more verification methods before granting access to an account. This process significantly reduces the risk of unauthorized access, even if a password is compromised. Here, we break down the different types of MFA:
- Something You Know: This could be a password, PIN, or an answer to a security question.
- Something You Have: This refers to a physical device, such as a smartphone or a smart card, which receives a verification code.
- Something You Are: This involves biometric verification like fingerprint scanning or facial recognition.
Setting Up Multi-factor Authentication
Setting up MFA is a straightforward process that significantly enhances your account security. Here, we guide you step-by-step on how to set up MFA for your online accounts:
Step 1. Choose the Right MFA Method
Depending on the service provider, choose an MFA method that suits your needs and preferences.
Step 2. Enable MFA in Settings
Visit the security settings of your online account and enable the multi-factor authentication option.
Step 3. Follow the Setup Instructions
Follow the on-screen instructions to set up MFA, which might involve verifying your identity through different methods.
Step 4. Test the Setup
Once set up, test the MFA to ensure it is working correctly and you are familiar with the process.
Benefits of Using Multi-factor Authentication
Implementing Multi-Factor Authentication (MFA) significantly bolsters your online security, offering a myriad of benefits. Firstly, it adds an extra layer of defense, making unauthorized access to your account considerably more challenging.
Moreover, it serves as a robust shield against phishing attempts; even if a cybercriminal manages to acquire your password, the second verification step acts as a barrier, preventing unauthorized access. Furthermore, the utilization of MFA grants users peace of mind, instilling confidence as they navigate the online realm, assured in the knowledge that their accounts enjoy heightened protection.
Password Change Reminders: Your First Line of Defense
As we forge ahead in our comprehensive guide to password management, we now spotlight the significance of password change reminders, a proactive strategy that serves as your first line of defense against potential cyber threats. In this section, we will elucidate why regular password changes are necessary and how to set up reminders effectively to enhance your online security.
Why Regular Password Changes are Necessary
In the ever-evolving landscape of cyber threats, maintaining the same password for extended periods can be a potential vulnerability. Regular password changes are a vital practice in safeguarding your online accounts from unauthorized access. Here, we delineate the reasons why it is essential:
- Mitigating the Risk of Breaches: Changing passwords regularly reduces the risk of data breaches, as cybercriminals often use compromised passwords to gain unauthorized access.
- Preventing Unauthorized Access: In case your password has been unknowingly compromised, changing it regularly prevents unauthorized users from maintaining access to your account.
- Protecting Sensitive Information: Regular password changes ensure that your personal and financial information remains secure, safeguarding you from potential fraud and identity theft.
Setting Up Password Change Reminders
To facilitate regular password changes, setting up reminders can be a handy tool. Here, we guide you through the process of setting up password change reminders:
Step 1. Utilize Password Managers
Many password managers come with built-in features to set up password change reminders, helping you to keep track of your password change schedule.
Step 2. Calendar Alerts
Use digital calendars to set up periodic reminders for password changes, ensuring you do not overlook this vital security practice.
Step 3. Custom Reminders
Some platforms offer custom reminders where you can set up personalized notifications for password changes, helping you maintain a secure online presence.
Tips for Creating Strong Passwords
As you embark on the journey of regular password changes, here are some tips to create strong and secure passwords:
- Complexity: Create passwords with a combination of uppercase and lowercase letters, numbers, and special characters.
- Length: Ensure your passwords are at least 12-16 characters long to enhance security.
- Unpredictability: Avoid using easily guessable information such as birthdays, names, or common phrases.
- Unique Passwords: Avoid reusing passwords across different platforms to prevent a single breach from compromising multiple accounts.
Password Recovery Solutions: Preparing for the Unexpected
As we continue our journey through the comprehensive guide to password management, we now turn our attention to password recovery solutions. In this section, we will explore the importance of having robust recovery solutions in place and guide you through setting up recovery options to ensure you are well-prepared for any unexpected events.
Importance of Password Recovery Solutions
In the dynamic digital realm, the frequent forgetting of passwords is a commonplace issue. Hence, the implementation of dependable password recovery solutions is essential, serving as a cornerstone of online security. These solutions not only facilitate swift and hassle-free access to your accounts but also prevent permanent lockouts, thereby protecting your valuable digital assets.
Moreover, they incorporate multiple verification steps, adding an additional tier of security to your accounts, making them an indispensable tool in safeguarding your online presence.
Setting Up Password Recovery Options
Setting up recovery options is a proactive approach to safeguarding your online presence. Here, we guide you through the process of setting up robust password recovery solutions:
Step 1. Email Recovery: Set up recovery through your email address, where a reset link or code will be sent to your registered email.
Step 2. Phone Number Recovery: Utilize your phone number as a recovery option, where a verification code can be sent via SMS or a call.
Step 3. Security Questions: Set up security questions that only you would know the answers to, adding a personal layer of security.
Step 4. Biometric Recovery: In certain platforms, you can set up biometric recovery options, such as fingerprint or facial recognition, for a secure and quick recovery process.
Best Practices for Password Recovery
To foster a secure and efficient password recovery process, it is imperative to adhere to several best practices. Firstly, make it a habit to periodically update your recovery options, ensuring they remain current and easily accessible. Secondly, opt for unique security questions that aren’t easily deciphered by others, adding a personal layer of security to your accounts.
Additionally, safeguard your recovery email and phone number, restricting access to yourself alone. Lastly, enhance your account security by utilizing multi-step verification during the recovery process wherever feasible, thereby adding an extra layer of protection against unauthorized access.
Beyond Passwords: Exploring Passkeys and FIDO
As we approach the culmination of our comprehensive guide to password management, it’s time to cast our gaze towards the future. In this section, we will explore the evolving landscape of digital security, focusing on innovative approaches like passkeys and the role of FIDO (Fast Identity Online) in shaping a more secure digital future.
What are Passkeys?
In the quest for enhanced digital security, the concept of passkeys is emerging as a promising alternative to traditional passwords. Passkeys, also known as security keys or physical keys, are devices that authenticate your identity without the need for a password. Here, we delve into the nuances of passkeys:
- Physical Device: A passkey is a physical device that you can carry with you, which is used to authenticate your identity during login.
- Biometric Verification: Some passkeys come equipped with biometric features, allowing for secure and quick authentication using fingerprint or facial recognition.
- Phishing Protection: Passkeys offer protection against phishing attacks, as they require physical possession of the key to authenticate, making unauthorized access nearly impossible.
Understanding FIDO and Its Benefits
FIDO, or Fast Identity Online, represents a revolutionary step in enhancing online security through its technology-agnostic security specifications that facilitate strong authentication. Leading the charge towards a future devoid of passwords, FIDO promises not only a fortified defense against password breaches but also a streamlined user experience.
By introducing swift and straightforward authentication processes, including biometric verification and the utilization of passkeys, it aims to foster a seamless user interface. Furthermore, its interoperable standards ensure compatibility across various devices and platforms, heralding a unified approach to online security that combines robust protection with user-friendliness.
How to Set Up and Use Passkeys
Setting up and using passkeys is a straightforward process that enhances your online security. Here, we guide you through the steps involved:
- Purchase a Passkey: Obtain a passkey from a reputable vendor. These are usually available as USB devices or as NFC-enabled devices for mobile phones.
- Register Your Passkey: Register your passkey with the online services that support FIDO authentication. This process usually involves following the setup instructions provided by the service.
- Using Your Passkey: To use your passkey, insert it into your device or use NFC to authenticate your identity during login, offering a secure and hassle-free login experience.
Conclusion
As we wrap up our in-depth journey into password management, we are now equipped with essential tools to safeguard our expanding digital domains. This guide highlights the vital role of strong password management in protecting our digital identities amidst escalating cyber threats. From understanding password encryption to adopting multi-factor authentication, we are guided towards a secure digital space.
Looking forward, we anticipate a shift in the digital landscape with the advent of innovative solutions like passkeys and FIDO standards, promising enhanced security and user convenience. As we adapt to this evolving sphere, staying abreast of these advancements is crucial. Let this guide steer you towards a future where digital safety is not a mere aspiration but a concrete reality.


Leave a Reply