
How to Encrypt Your Emails for Maximum Privacy
In today’s digital age, where communication is predominantly online, the security of our messages has become paramount. Emails, in particular, are a primary mode of communication for both personal and professional purposes. They carry sensitive information, from bank details and business strategies to personal photos and intimate conversations. But how often do we pause and consider the safety of these digital letters we send out into the vast expanse of the internet?
The Digital Postcard Analogy
Imagine sending postcards for all your correspondence, be it a bank statement, a love letter, or a business proposal. Anyone handling that postcard, from the postman to a passerby, can read its content. Traditional emails, when unencrypted, are much like these postcards—visible to many eyes. They might pass through multiple servers, each a potential point of vulnerability, before reaching their intended recipient.
| Traditional Email | Encrypted Email |
|---|---|
| Like a postcard | Like a sealed envelope |
| Visible content | Hidden content |
| Vulnerable to snooping | Secure and private |
The Current State of Email Privacy
While many email services encrypt emails during transmission, they often store them in clear text. This storage method makes them readable by third parties, including the email service providers themselves. Popular platforms like Gmail and Outlook, by default, do not offer end-to-end encryption. This lack of comprehensive encryption means that, without taking additional measures, our emails are potentially exposed to prying eyes.
Understanding Email Encryption: The Digital Lock and Key
As we delve into the world of email encryption, it’s essential to grasp its foundational concepts. At its core, email encryption is like a digital lock and key mechanism, ensuring that only the intended recipient can “unlock” and read the email.
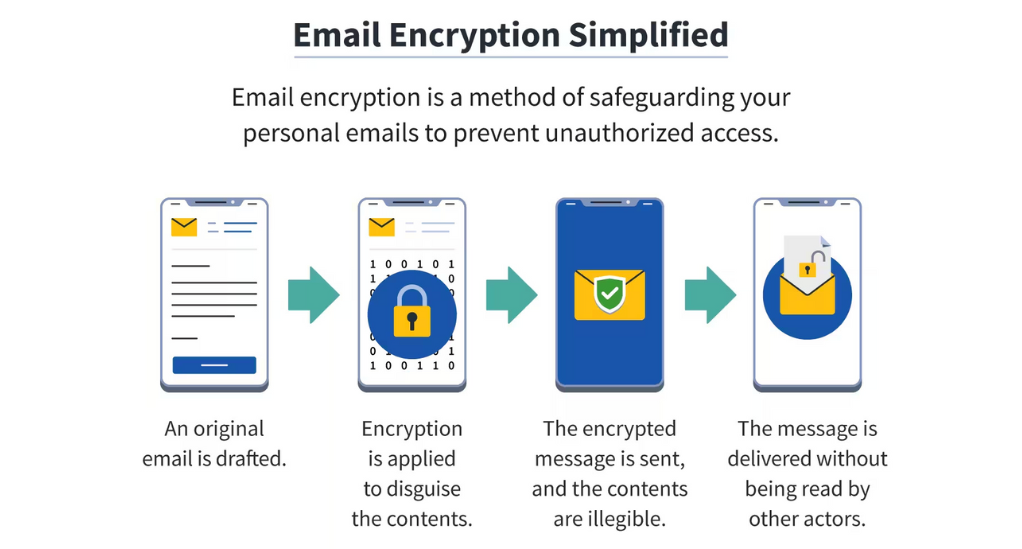
What is Email Encryption?
Email encryption is the process of converting email content into a coded version, rendering it unreadable to anyone except the holder of the decryption key. In simpler terms, it’s like converting your email into a secret language that only you and your intended recipient understand.
Why Email Encryption Matters
- Data Breaches: In an era where data breaches are becoming increasingly common, encrypted emails ensure that even if hackers access your emails, they won’t be able to decipher the content.
- Confidentiality: Whether you’re sharing business secrets, personal information, or sensitive documents, encryption ensures that your email’s content remains confidential.
- Regulatory Compliance: For businesses, especially those in sectors like healthcare or finance, encrypting emails can be a requirement to comply with data protection regulations.
- Trust: Knowing that your emails are encrypted can build trust with your recipients, assuring them that you prioritize their privacy and data security.
The Mechanics of Email Encryption
To understand the mechanics, let’s break down the process:
| Step | Description |
|---|---|
| Encryption | Transforming email into ciphertext |
| Transmission | Sending the unreadable email |
| Decryption | Converting the email back to its original form |
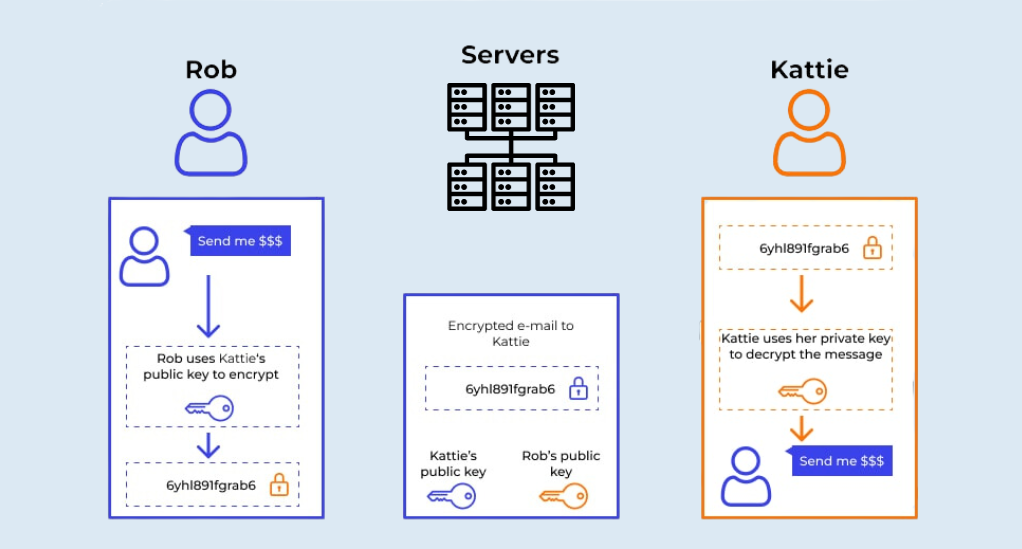
The Two Key System: Public and Private
One of the most common methods of email encryption is the public key infrastructure (PKI). Here’s how it works:
- Public Key: This is a key that you can share with anyone. It’s used to encrypt the email.
- Private Key: This key remains confidential and is used to decrypt the email. Only the intended recipient, who has the private key, can decrypt and read the email.
The Vulnerabilities of Unencrypted Emails: The Open Book Dilemma
Before diving deeper into the solutions, it’s crucial to understand the problems. Unencrypted emails, as mentioned, are akin to postcards. But what does this mean in practical terms? And what are the risks associated with sending emails in their raw, unencrypted form?
The Journey of an Email
When you hit ‘send’ on an email, it doesn’t directly teleport to your recipient’s inbox. Instead, it traverses a complex network of servers, routers, and data centers. At each point in this journey, the email is vulnerable to interception.
Potential Threats to Unencrypted Emails
- Eavesdropping: Just as someone might overhear a conversation in a cafe, cyber eavesdroppers can ‘listen in’ on unencrypted emails as they travel across the internet.
- Man-in-the-Middle Attacks: Here, a malicious actor intercepts the email communication between the sender and the recipient, potentially altering the email’s content without either party’s knowledge.
- Data Storage Vulnerability: Even after your email reaches its destination, it’s stored on email servers. If these servers aren’t secure, your stored emails can be accessed and read by unauthorized parties.
- Legal and Unauthorized Access: Some governments and organizations can legally access emails for various reasons, from criminal investigations to surveillance. Without encryption, the content of these emails is readily available.
Real-world Consequences
- Identity Theft: Personal details shared via unencrypted emails can be used for identity theft, leading to financial fraud and other malicious activities.
- Business Espionage: For businesses, unencrypted emails can be a goldmine for competitors, revealing strategies, client information, and more.
- Personal Repercussions: Sensitive personal information, when leaked, can lead to blackmail, public humiliation, or even personal harm.
A Glimpse at Popular Email Services
While services like Gmail and Outlook are household names, their default settings don’t offer end-to-end encryption. This means that while your email might be encrypted as it travels from your device to Gmail’s servers (and vice versa), Google can access and read your emails while they’re stored on their servers.
Public-Key Cryptography in Email Encryption: The Twin Key Paradigm
Having established the vulnerabilities of unencrypted emails, it’s time to delve deeper into one of the primary mechanisms that offer a solution: Public-Key Cryptography. This system, often likened to a twin key paradigm, is the backbone of many email encryption methods.
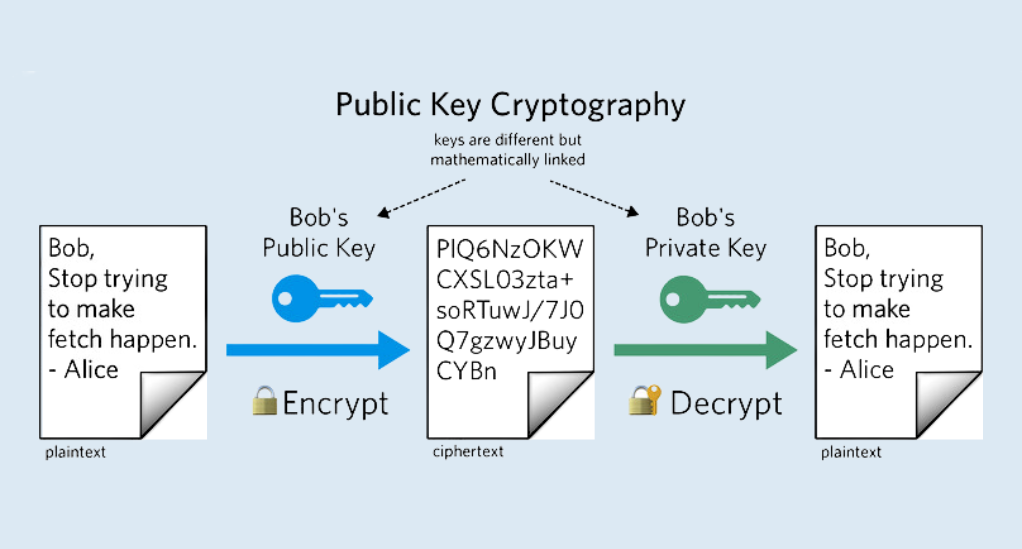
Decoding Public-Key Cryptography
At its essence, Public-Key Cryptography involves two keys: a public key, which is available to anyone, and a private key, which remains confidential to the user. These keys work in tandem to ensure the security of the email content.
- Encryption with the Public Key: When someone wants to send you an encrypted email, they use your public key to encrypt the message. Once encrypted with this key, the content can only be decrypted using the corresponding private key.
- Decryption with the Private Key: Upon receiving the encrypted email, you use your private key to decrypt and read the message. This ensures that even if someone intercepts the email, they cannot decipher its content without the private key.
Benefits of Public-Key Cryptography
- Security: As the private key remains confidential and is not transmitted over the internet, the chances of unauthorized decryption are minimal.
- Simplicity for Senders: Senders don’t need to manage multiple encryption keys for different recipients. They simply use the recipient’s public key, which is readily available.
- Digital Signatures: Beyond encryption, the system can be used to create digital signatures. Senders can use their private key to sign a message, and recipients can use the sender’s public key to verify the authenticity of the message.
Transport-Level vs. End-to-End Encryption: Choosing the Right Shield
As we navigate the realm of email encryption, two terms frequently emerge: Transport-Level Encryption and End-to-End Encryption. Both serve the noble purpose of safeguarding our digital correspondence, but they operate differently and offer varying levels of protection. Let’s dissect these methods to understand which shield is best suited for our needs.
Transport-Level Encryption: The Guarded Transit
Imagine a secure armored van transporting a valuable item. While the item is safe inside the van during its journey, it can be accessed by authorized personnel at the starting and ending points. This is analogous to Transport-Level Encryption.
How it Works:
- Encryption at Source: When you send an email, it’s encrypted as it leaves your device or email client.
- Secure Transit: The email remains encrypted as it travels through the internet, ensuring it’s shielded from potential eavesdroppers or interceptors.
- Decryption at Destination: Upon reaching the email service provider’s server, the email is decrypted. It’s then re-encrypted for its journey to the recipient’s device, where it’s decrypted again for reading.
Pros:
- Ease of Use: This method is often automatically implemented by email service providers, requiring no additional steps from the user.
- Protection in Transit: It ensures that emails are secure as they travel across the internet.
Cons:
- Vulnerable Storage: Once the email reaches the service provider’s servers, it’s decrypted and can be accessed by the provider. This poses a risk if the servers are compromised.
End-to-End Encryption: The Sealed Envelope
Think of sending a letter in a sealed envelope, which can only be opened by the recipient. No one, not even the postal service handling the delivery, can peek inside. This represents End-to-End Encryption.
How it Works:
- Encryption at Source: The email is encrypted right at the source, on your device.
- Secure Transit and Storage: The email remains encrypted, both in transit and when stored on the email servers. Only the intended recipient, with the right decryption key, can access its content.
- Decryption at Destination: The email is decrypted only at the endpoint, i.e., the recipient’s device.
Pros:
- Complete Privacy: Offers the highest level of privacy, ensuring that no one, not even the email service provider, can access the email’s content.
- Secure Storage: Emails remain encrypted on servers, safeguarding against potential server breaches.
Cons:
- Complexity: Setting up end-to-end encryption often requires additional tools or plugins. Both the sender and recipient need to use compatible systems.
Popular Email Encryption Protocols: Navigating the Digital Locksmith’s Toolkit
With a foundational understanding of the types of email encryption, it’s time to explore the specific protocols and tools that make this encryption possible. These protocols are the digital locksmith’s tools, each designed for specific scenarios and offering unique features.
| Protocol | Description | Pros | Cons |
|---|---|---|---|
| STARTTLS | A protocol extension that upgrades the connection to encrypted communication. | – Flexibility with both encrypted and unencrypted communications. – Widespread adoption by many email services. | – Opportunistic encryption can lead to unencrypted fallbacks. – Vulnerable to downgrade attacks. |
| OpenPGP | A data encryption standard using public key cryptography. | – Robust end-to-end encryption. – Allows for digital signatures to verify authenticity. | – Setting up and managing key pairs can be challenging for some users. |
| S/MIME | Uses a system of digital certificates to encrypt and decrypt emails. | – Certificates offer added authenticity. -Natively supported by many email clients. | – Heavily reliant on the integrity of the issuing Certificate Authority. |
Setting Up and Using Email Encryption: A Step-by-Step Guide
In the digital age, ensuring the privacy of our emails is paramount. While understanding the importance and mechanisms of email encryption is crucial, it’s equally vital to know how to implement these measures. In this section, we’ll provide a comprehensive guide on setting up and using email encryption, ensuring your digital correspondence remains confidential.
Choosing the Right Encryption Method
Before diving into the setup, it’s essential to select the encryption method that best suits your needs:
| Method | Best For | Considerations |
|---|---|---|
| STARTTLS | Casual users and businesses looking for a basic level of security | Requires both sender and receiver’s email servers to support STARTTLS |
| OpenPGP | Those seeking robust end-to-end encryption | Requires both parties to set up and manage key pairs |
| S/MIME | Users and businesses preferring certificate-based encryption | Relies on trusted Certificate Authorities for issuing certificates |
Setting Up STARTTLS
- Email Clients: Most modern email clients, like Outlook and Thunderbird, support STARTTLS by default. Ensure it’s enabled in the settings.
- Webmail Services: Platforms like Gmail and Yahoo Mail use STARTTLS automatically. No user intervention is required.
Implementing OpenPGP
- Download a PGP Tool: Tools like GnuPG (for Windows) or MacGPG (for Mac) are essential for generating key pairs and managing encryption.
- Generate Key Pair: Once installed, use the tool to create a public-private key pair.
- Share Public Key: Distribute your public key to contacts. This can be done via email or by uploading it to a public key server.
- Encrypting Emails: When composing an email, use your email client’s encryption option, selecting the recipient’s public key for encryption.
Using S/MIME
- Obtain a Digital Certificate: Apply for a digital certificate from a trusted Certificate Authority (CA) like Comodo or DigiCert.
- Install the Certificate: Once received, install the certificate in your email client. This process varies depending on the client but is generally found in the security settings.
- Sending Encrypted Emails: When composing an email, select the encryption option in your email client. The client will use the recipient’s certificate for encryption.
Challenges and Solutions
While email encryption significantly enhances security, it’s not without challenges:
- Key/Certificate Management: Losing your private key or certificate means you can’t decrypt emails. Solution: Regularly backup keys and certificates in secure locations.
- Compatibility Issues: Not all email clients or services support every encryption method. Solution: Ensure both sender and recipient use compatible systems or tools.
- User Error: Accidentally sending unencrypted emails or sharing private keys can compromise security. Solution: Regularly educate and remind yourself about best practices.
Encrypted Email Providers: The Fortresses of Digital Correspondence
While individual encryption methods offer a robust layer of security, there’s a growing demand for email services that prioritize encryption and privacy by default. These providers have built their platforms around the core principle of safeguarding user data. Let’s explore some of the notable encrypted email providers and understand their offerings.
ProtonMail: The Swiss Vault
Originating from the CERN research facility, ProtonMail has quickly become synonymous with email privacy.
Features:
- End-to-End Encryption: Emails are encrypted on your device and can only be decrypted by the recipient.
- Zero Access: ProtonMail’s servers are designed so that they cannot access or read user emails.
- Open Source: Transparency is key, and ProtonMail’s open-source nature allows for community scrutiny and trust.
Tutanota: The German Sentinel
Tutanota, derived from Latin words meaning “secure message,” is another heavyweight in the encrypted email arena.
Features:
- Automatic Encryption: All emails, even those sent to non-Tutanota users, are encrypted.
- Stripped Metadata: Unlike many providers, Tutanota encrypts email metadata, offering an added layer of privacy.
- Integrated Calendar: A unique feature, Tutanota offers an encrypted calendar, ensuring all your appointments remain private.
Hushmail: The Veteran Guardian
One of the pioneers in encrypted email services, Hushmail has been guarding communications since 1999.
Features:
- Simplified Encryption: Hushmail automates the encryption process, making it user-friendly even for those unfamiliar with encryption.
- Custom Domains: Particularly appealing to businesses, Hushmail allows users to have encrypted email addresses on their own domains.
- Secure Web Forms: Beyond emails, Hushmail offers encrypted web forms, ideal for businesses collecting sensitive information.
| Provider | Origin | Unique Feature |
|---|---|---|
| ProtonMail | Switzerland | Open Source |
| Tutanota | Germany | Encrypted Calendar |
| Hushmail | Canada | Secure Web Forms |
Choosing the Right Provider
When selecting an encrypted email provider, consider the following:
- Jurisdiction: The provider’s location can impact user data due to local laws and regulations.
- Features: Beyond encryption, look for features like storage capacity, custom domains, and additional tools.
- Usability: An encrypted email service should be user-friendly, ensuring that privacy doesn’t come at the expense of convenience.
Conclusion
In an era marked by increasing cyber threats and data breaches, the significance of email encryption extends beyond mere technical protection; it symbolizes our collective commitment to digital privacy. As individuals and businesses become more digitally intertwined, the tools we’ve discussed offer a robust shield, safeguarding our personal and professional communications. However, challenges like adoption rates and regulatory hurdles persist. Despite these, the rise of user-friendly encrypted email providers and the unwavering support of the open-source community provide hope.
As users, our choices can shape the digital landscape. By prioritizing encryption, we not only secure our data but also advocate for a broader cultural shift towards digital privacy. The tools are in our hands, and the onus is on us to champion a digital world where communication is both free and secure. The future of email encryption isn’t just about technology; it’s about envisioning and creating a digital realm grounded in trust and confidentiality.


Leave a Reply