
How to Choose the Right Antivirus Software for Your Device
In today’s interconnected world, our devices are more than just tools; they are extensions of ourselves. From personal photos to bank details, they store fragments of our lives, making their protection paramount. As cyber threats evolve in complexity and frequency, the need for robust antivirus software has never been more critical. But with a plethora of options available, how does one make an informed choice?
The Digital Landscape and Its Challenges
The digital age, while bringing unparalleled convenience, has also ushered in unique challenges. Cyberattacks are no longer limited to large corporations or governments. Individual users are increasingly becoming targets, with cybercriminals exploiting vulnerabilities for financial gain, data theft, or simply to cause disruption.
| Cyber Threat | Description | Potential Impact |
|---|---|---|
| Malware | Malicious software designed to damage or exploit any device, network, service, or program. | Data theft, system damage, unauthorized access. |
| Phishing | Fraudulent attempts to obtain sensitive information by disguising oneself as a trustworthy entity. | Financial loss, identity theft. |
| Ransomware | A type of malware that threatens to publish the victim’s data or block access to it unless a ransom is paid. | Data loss, financial loss. |
| Spyware | Software that aims to gather information about a person or organization without their knowledge. | Privacy invasion, data theft. |
The Role of Antivirus Software
Antivirus software acts as a gatekeeper, monitoring incoming and outgoing data for potential threats. It’s not just about detecting viruses anymore. Modern antivirus solutions are equipped to handle a range of threats, from ransomware to phishing attacks. They employ sophisticated algorithms and real-time threat intelligence to identify and neutralize threats before they can cause harm.
However, not all antivirus solutions are created equal. The right software should align with your device’s operating system, your usage patterns, and, importantly, your understanding of digital threats. As we delve deeper into this guide, we’ll explore the nuances of choosing the right antivirus software, ensuring that your digital life remains uncompromised.
Understanding Major Threats
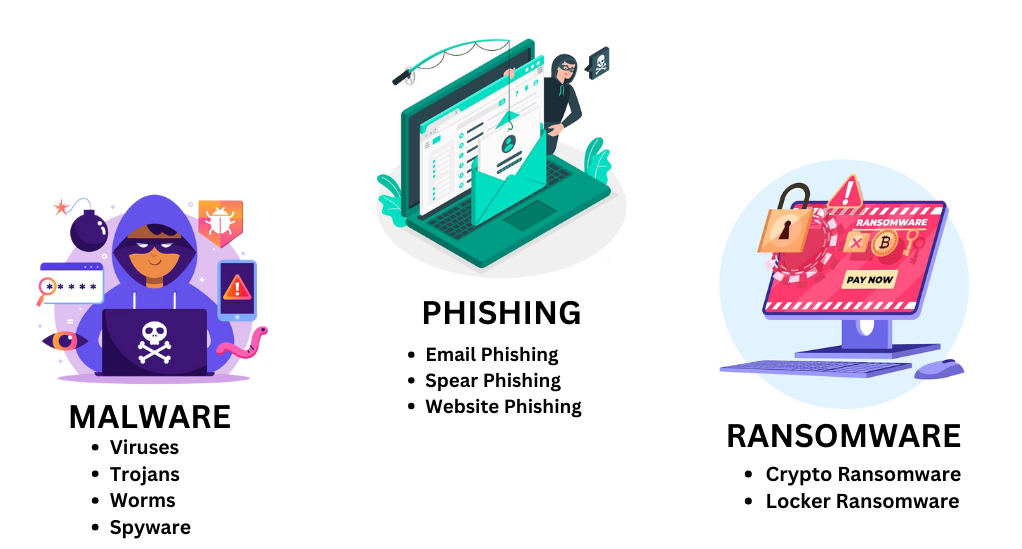
In the vast realm of cyberspace, threats lurk in every corner. From seemingly harmless emails to compromised software updates, cybercriminals have honed their skills to exploit even the slightest vulnerability. To make an informed choice about antivirus software, it’s essential first to understand the major threats you’re up against.
Malware: The Silent Invader
Malware, short for malicious software, encompasses various programs designed with ill intent. These can range from viruses that replicate themselves to damage system operations to spyware that silently monitors user activities.
- Viruses: These are malicious programs that can replicate themselves and spread to other computers. They can corrupt or delete data, use email programs to spread to other computers, or even erase everything on a hard disk.
- Trojans: Unlike viruses, Trojans do not replicate themselves but pave the way for other malicious software to enter and damage your system.
- Worms: Worms are a type of malware that spread across computer networks by exploiting vulnerabilities. They can consume bandwidth, leading to system slowdowns.
- Spyware: This type of malware secretly monitors and collects information from the user’s device, often leading to identity theft or financial loss.
Phishing: The Art of Deception
Phishing attacks are deceptive tactics used by cybercriminals to trick users into revealing sensitive information, such as passwords or credit card numbers. These attacks often come in the form of authentic-looking emails or websites, making it challenging for users to distinguish between genuine and fake.
- Email Phishing: Cybercriminals send fraudulent emails that appear to be from reputable sources, urging users to click on a link or download an attachment, leading to potential malware infections or data theft.
- Spear Phishing: This is a more targeted form of phishing where the attacker customizes their trap for a specific individual or organization.
- Website Phishing: Here, attackers create fake websites that mimic real ones, tricking users into entering their credentials, which are then stolen.
Ransomware: The Digital Kidnapper
Ransomware is a particularly malicious form of malware that encrypts the victim’s data, rendering it inaccessible. The attacker then demands a ransom, usually in cryptocurrency, to decrypt the data. Two primary types of ransomware are:
- Crypto Ransomware: This type encrypts valuable data on the victim’s computer, making it inaccessible until a ransom is paid.
- Locker Ransomware: Instead of encrypting files, this type locks the victim out of their device, demanding payment to regain access.
The Importance of Awareness
While antivirus software plays a crucial role in defending against these threats, user awareness is equally vital. Recognizing suspicious emails, avoiding downloads from untrusted sources, and regularly updating software can significantly reduce the risk of a cyberattack.
The Need for Real-Time Prevention
While understanding threats is the first step, relying solely on reactive measures can leave gaps in your digital defense. In the ever-evolving world of cyber threats, real-time prevention is not just a luxury; it’s a necessity. Let’s explore why proactive protection is crucial and what it entails.
Proactive vs. Reactive: The Digital Shield and Sword
Imagine your device as a fortress. Reactive measures act as guards that respond once the enemy breaches the walls, while proactive measures are the fortified walls, moats, and watchtowers that prevent the enemy from entering in the first place.
- Reactive Measures: These are actions taken after a threat has been identified. It includes quarantining infected files, alerting the user, and removing malware. While essential, relying solely on reactive measures can sometimes be too late, especially with ransomware that can quickly encrypt your files.
- Proactive Measures: These are preemptive actions that stop threats before they can cause harm. It involves real-time scanning, monitoring suspicious behavior, and blocking known malicious websites.
Key Features of Proactive Protection
- Real-time Scanning: Instead of waiting for a scheduled scan, real-time scanning continuously monitors your device for potential threats. It checks files as they’re accessed, ensuring malware doesn’t get a chance to execute.
- Behavioral Analysis: Beyond just known threats, modern antivirus software can monitor software behavior. If a program starts acting similarly to known malware after an update, the antivirus can flag it, even if the specific threat isn’t in its database.
- Web Browsing Protection: A significant portion of threats comes from the web, be it malicious downloads or phishing sites. Web protection features alert users when they’re about to visit a potentially harmful site, blocking access to known malicious URLs.
- Firewall Integration: A robust firewall acts as a gatekeeper, controlling incoming and outgoing traffic based on security policies. Integrated with antivirus software, it can provide an additional layer of protection against threats.
- Automatic Updates: Cyber threats are continually evolving, and so must our defenses. Automatic updates ensure that the antivirus software is equipped with the latest definitions and threat intelligence.
The Power of Cloud-Based Threat Intelligence
With the advent of cloud computing, many antivirus solutions now leverage cloud-based threat intelligence. This approach allows software to access vast databases of threat information in real-time, ensuring up-to-date protection without heavy on-device databases. It also enables faster dissemination of new threat definitions to all users.
Efficiency and Accuracy of Antivirus Software
In the vast sea of antivirus solutions, two critical factors set the best apart from the rest: efficiency and accuracy. While it’s essential for software to detect and neutralize threats, it’s equally vital that it does so without compromising your device’s performance or producing a barrage of false alarms.
The Delicate Balance: Performance vs. Protection
Every software, including antivirus, uses device resources. The key is balancing protection without compromising speed. System overhead measures the resources an antivirus uses, with lightweight versions ensuring faster device performance. While real-time scanning is vital, it’s equally important for the software to conduct quick full system scans to catch unnoticed threats.
Precision Matters: The Threat of False Positives
In antivirus software, accurate threat detection is vital. It’s not just about identifying real threats but also avoiding false positives, where benign files are mistakenly marked as harmful. Such errors can lead to important files being quarantined or deleted. A reliable antivirus should have a high threat detection rate while minimizing false positives, ensuring both security and user trust.
Benchmarking and Independent Testing
Several organizations, like AV-Comparatives and AV-TEST, routinely evaluate antivirus software. Their tests gauge the software’s defense capabilities against known and new threats, its impact on device performance, and overall user-friendliness, including the rate of false positives.
Relying on these independent tests can provide an objective perspective on the efficiency and accuracy of different antivirus solutions.
Ease of Use and User Experience
In the realm of antivirus software, technical prowess is undeniably vital. However, the best of features can fall short if they’re not user-friendly. After all, the most secure system is one where the user, empowered by intuitive tools, can confidently navigate the digital world.
The Significance of a User-Friendly Interface
A well-crafted user interface (UI) is more than just visually appealing; it streamlines complex tasks for users of all tech levels. Features like the “Dashboard Overview” offer a quick system health check, while “Easy Customization” allows tailored adjustments. Crucially, “Clear Alerts” promptly inform users of threats and suggest next steps.
Automatic Updates: Staying Ahead of Threats
In the ever-evolving landscape of cyber threats, outdated software can be a significant vulnerability. Hence, the importance of automatic updates:
- Seamless Integration: Updates should integrate seamlessly, ensuring that the latest threat definitions and software improvements are implemented without user intervention.
- Minimal Disruption: While updates are crucial, they shouldn’t disrupt the user’s activities. Scheduling them during idle times or ensuring they don’t hog system resources can enhance user experience.
Competent Customer Support: A Helping Hand
Even with user-friendly software, challenges may arise. Robust customer support is essential, offering multiple contact methods like live chat, email, or phone. A detailed knowledge base can help users resolve minor issues independently, while swift and knowledgeable support enhances user trust and satisfaction.
Exploring Additional Features
Beyond the primary functions of threat detection and neutralization, many antivirus solutions offer a suite of additional features. These tools, while not essential, can significantly enhance the overall protection of your device and provide added convenience.
Password Managers: The Digital Vault
Integrated password managers offer more than just a safe place to store passwords. They provide a secure vault for storing and auto-filling login details, ensuring convenience without compromising security. Additionally, they can generate strong passwords, ensuring optimal protection against potential breaches.
System Performance Optimization Tools
Over time, devices can become sluggish due to redundant files or unnecessary background processes. Antivirus solutions with system performance optimization tools can rejuvenate these devices. They clear out redundant files, manage background processes, and ensure that the device runs efficiently, enhancing the overall user experience.
Online Privacy and Data Breach Alerts
In today’s digital age, online privacy is a growing concern. Some antivirus tools address this by offering VPN integrations, allowing users to browse the internet anonymously. Additionally, data breach alerts notify users if their personal information has been exposed in known breaches, allowing them to take preventive measures.
Home Network Monitoring
With the rise of smart devices, home networks have become more complex and vulnerable. Antivirus solutions with home network monitoring features help users secure these networks. They offer Wi-Fi security checks, ensuring optimal settings for security, and provide an inventory of all devices connected to the network, ensuring no unauthorized devices are accessing it.
Making the Final Decision
With a plethora of antivirus solutions available, each boasting a myriad of features, making the final decision can be daunting. However, by considering a few key factors, you can ensure that your choice aligns perfectly with your needs.
Device Compatibility: One Size Doesn’t Fit All
Different devices operate on various systems, and it’s essential to choose antivirus software that’s compatible with your specific platform. Whether you’re using Windows, macOS, or mobile devices like Android and iOS, the antivirus solution should cater to your device’s unique requirements, ensuring seamless protection.
Multi-Device and Family Protection: Covering All Bases
In today’s interconnected world, many of us use multiple devices. Antivirus solutions that offer multi-device licenses ensure comprehensive coverage across all your devices. Additionally, family plans can protect devices used by all family members, often at a discounted rate, ensuring collective security.
Assessing the Software’s Feature Set
While a plethora of features can seem impressive, it’s essential to prioritize based on your specific needs. Core protection features, such as real-time scanning and threat detection, should be non-negotiable. However, depending on your usage patterns, you might also value additional features like password managers or system optimization tools.
Budget Considerations: Value for Money
While free antivirus solutions might seem appealing, they often lack advanced features. It’s crucial to assess subscription plans, ensuring you get the features you need without overpaying. Additionally, solutions that offer trial periods allow you to test the software firsthand, ensuring it meets your expectations before committing.
User Reviews and Expert Opinions: Peer Insights
Technical specifications provide a foundation, but insights from actual users can offer invaluable perspectives. Platforms like Trustpilot or app store reviews can highlight potential issues or user-favored features. Additionally, expert reviews from organizations like AV-Comparatives or AV-TEST provide objective assessments of the software’s effectiveness and reliability.
Conclusion
In our increasingly digital world, the importance of safeguarding our devices and data cannot be overstated. The right antivirus software acts as a sentinel, offering proactive protection against a myriad of cyber threats. However, technology alone isn’t the complete answer. Users, armed with awareness and vigilance, play a crucial role in this defense matrix. As we embrace the conveniences of the digital age, it’s imperative to prioritize security, ensuring that our personal and professional lives remain uncompromised and thriving in a safe digital environment.


Leave a Reply