
How to Stay Updated with Emerging Encryption Trends
In an era of rising data breaches and cyber threats, the significance of encryption and emerging encryption trends is paramount. Encryption is the art and science of coding information to block unauthorized access. As our digital footprint grows, the demand for advanced encryption techniques to protect our data intensifies.
Why is Encryption Crucial in Today’s Digital Age?
The digital age has brought about unprecedented levels of connectivity and convenience. From online banking to social media interactions, our lives are intertwined with the digital realm. However, this convenience comes at a cost. Every digital interaction we make is a potential entry point for cybercriminals. Encryption acts as the first line of defense, ensuring that even if data is intercepted, it remains indecipherable and useless to unauthorized individuals.
| Year | Number of Data Breaches | Records Exposed | Significance |
|---|---|---|---|
| 2018 | 1,257 | 471 million | Rapid increase in cyberattacks targeting financial data |
| 2019 | 1,473 | 164.68 million | Personal data breaches, including healthcare information |
| 2020 | 1,108 | 300.57 million | Rise in ransomware attacks and state-sponsored cyber threats |
| 2021 | 1,291 | 155.8 million | Increased attacks on critical infrastructure and institutions |
Source: Statista (Note: This table is illustrative and may not represent actual data)
The evolving nature of cyber threats necessitates that encryption techniques also evolve. As hackers employ more sophisticated methods to breach defenses, the encryption community must stay one step ahead, constantly innovating and adapting to ensure data remains secure.
The Historical Evolution of Encryption
The journey of encryption is as old as the art of communication itself. Since ancient times, humans have sought ways to convey messages in secret, ensuring that only the intended recipient could decipher the true meaning. This section will take you through a brief history of encryption, highlighting its evolution and significance over the centuries.
Early Encryption Techniques: The Dawn of Secret Messages
One of the earliest known encryption techniques is the Caesar Cipher, named after Julius Caesar, who reportedly used it to protect his military communications. This method involved shifting each letter in the plaintext by a fixed number of positions in the alphabet. For instance, with a shift of 3, ‘A’ would become ‘D’, ‘B’ would become ‘E’, and so on.
| Original Letter | Shifted by 3 |
|---|---|
| A | D |
| B | E |
| C | F |
| … | … |
While rudimentary by today’s standards, the Caesar Cipher was effective in its time, primarily because the concept of encryption was not widely understood.
As civilizations advanced, so did their cryptographic techniques. The Scytale, used by ancient Greeks, involved wrapping a strip of parchment around a rod of a specific diameter. The message was then written lengthwise, and when unwound, it appeared as a jumble of letters, decipherable only when wrapped around a rod of the same diameter.
The Renaissance and the Rise of Complex Ciphers
The Renaissance period saw a surge in interest in cryptography, with polymaths like Leon Battista Alberti introducing the concept of polyalphabetic ciphers. Alberti’s cipher used two alphabets, switching between them at regular intervals, making decryption significantly more challenging without the key.
The Age of Machines: Enigma and Beyond
The 20th century marked a significant shift in encryption techniques with the advent of machines. The Enigma machine, used by the Germans during World War II, is a prime example. This electro-mechanical device allowed operators to select daily codes, making the encryption process more complex and the code harder to break. However, with the combined efforts of cryptanalysts like Alan Turing, the Allies managed to decipher Enigma-encrypted messages, significantly influencing the course of the war.
Public-Key Cryptography: A Modern Marvel
The late 20th century introduced a groundbreaking concept in encryption: public-key cryptography. Unlike traditional methods that used a single key for both encryption and decryption, public-key cryptography employs two keys: a public key for encryption and a private key for decryption. This technique forms the foundation of many modern encryption protocols, ensuring secure online transactions and communications.
Modern Encryption Techniques
As we transitioned into the digital age, the need for more robust and complex encryption methods became paramount. The vast amounts of data being transferred online required encryption standards that could withstand sophisticated cyberattacks. This section will explore some of the modern encryption techniques that have become the backbone of digital security.
From DES to Advanced Encryption Standards
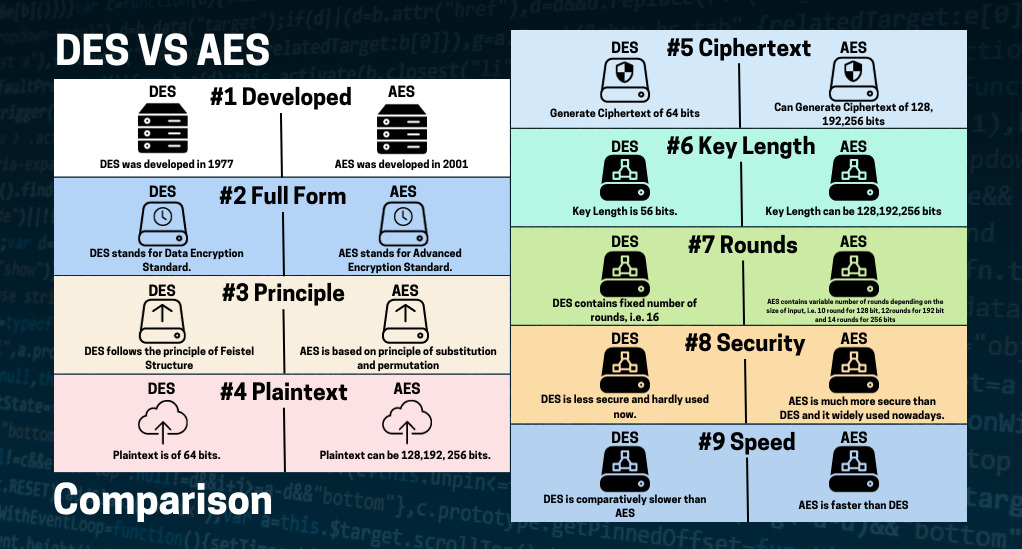
The Data Encryption Standard (DES), introduced in the 1970s, was one of the first symmetric-key algorithms for commercial use. It encrypts data in 64-bit blocks using a 56-bit key. However, with the advancement in computational power, DES became vulnerable to brute-force attacks, leading to its eventual decline.
Recognizing the limitations of DES, the Advanced Encryption Standard (AES) was introduced in the early 2000s. AES operates on block sizes of 128 bits and supports key lengths of 128, 192, or 256 bits, making it exponentially more secure than DES.
Comparison of DES and AES:
- Feature/Standard: DES vs. AES
- Key Length:
- DES: 56 bits
- AES: 128, 192, 256 bits
- Block Size:
- DES: 64 bits
- AES: 128 bits
- Security Level:
- DES: Moderate
- AES: Very High
- Vulnerabilities:
- DES: Brute-force
- AES: Few known
Other Noteworthy Modern Encryption Algorithms
- TwoFish: A symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It’s known for its speed and security.
- ChaCha20-Poly1305: A modern stream cipher that provides confidentiality and authenticity. It’s widely used in internet protocols, especially where speed and efficiency are crucial.
The Importance of Key Sizes and the Challenges of Brute-Force Attacks
In encryption, the key size matters. A longer key means that there are exponentially more possible keys to guess, making brute-force attacks (where attackers try every possible key) impractical. For instance, while a 56-bit key as in DES offers over 72 quadrillion possible combinations, a 256-bit key as in some AES configurations has an astronomically higher number of potential combinations.
However, it’s essential to understand that no encryption method is entirely immune to attacks. The goal is to make any attack as time-consuming and resource-intensive as possible, rendering it impractical.
The Role of Hardware in Encryption
Modern encryption doesn’t just rely on algorithms. Hardware plays a crucial role in ensuring data security. Hardware Security Modules (HSMs) are physical devices that safeguard and manage digital keys. They provide an added layer of security, preventing physical tampering and unauthorized access.
The Quantum Computing Challenge
The realm of encryption, like many other fields, is on the brink of a significant transformation with the advent of quantum computing. Quantum computers, with their ability to process vast amounts of data simultaneously using quantum bits or qubits, pose both opportunities and challenges for encryption. This section will delve into the implications of quantum computing on encryption and the race to stay ahead in the security game.
Understanding Quantum Computing
Traditional computers use bits as the smallest unit of data, which can be either a 0 or a 1. Quantum computers, on the other hand, use qubits. A qubit can be both 0 and 1 simultaneously, thanks to a phenomenon called superposition. This ability allows quantum computers to process a massive amount of possibilities at once, potentially solving complex problems in seconds that would take traditional computers millennia.
The Threat to Current Encryption Standards
Most of today’s encryption techniques, especially public-key cryptosystems like RSA and ECC, rely on the difficulty of certain mathematical problems (like factoring large numbers). For classical computers, these problems are time-consuming. However, quantum computers could potentially solve these problems much more quickly.
For instance, Shor’s algorithm, when run on a sufficiently powerful quantum computer, can factor large numbers exponentially faster than the best-known algorithms on classical computers. This capability could effectively break RSA encryption.
Potential Impact of Quantum Computing on Encryption:
- Encryption Method: RSA
- Vulnerability to Quantum Computing: Highly Vulnerable
- Notes: Shor’s algorithm can factor large numbers efficiently.
- Encryption Method: ECC
- Vulnerability to Quantum Computing: Vulnerable
- Notes: Quantum algorithms can solve the discrete logarithm problem faster.
- Encryption Method: AES
- Vulnerability to Quantum Computing: Moderately Resistant
- Notes: Key lengths might need to be doubled for the same security level.
- Encryption Method: TwoFish
- Vulnerability to Quantum Computing: Unknown
- Notes: Research is ongoing, but currently believed to be resistant.
The Race for Quantum-Resistant Algorithms
Recognizing the potential threat posed by quantum computing, researchers are already working on post-quantum cryptography. These are encryption methods designed to be secure against the immense computational power of quantum computers.
Several algorithms are being proposed and tested, including lattice-based cryptography, hash-based cryptography, and code-based cryptography, among others. The goal is to find methods that are both secure against quantum attacks and efficient for everyday use.
Staying Updated: Tools and Resources
In the ever-evolving landscape of encryption, staying informed is not just beneficial—it’s essential. As new threats emerge and technologies advance, professionals and enthusiasts alike must keep pace to ensure optimal data protection. This section will guide you through various tools, platforms, and resources that can help you stay updated with the latest in encryption trends.
Recommended Platforms and Journals
- IACR (International Association for Cryptologic Research): A non-profit organization dedicated to promoting cryptologic research. Their website offers a plethora of publications, conference updates, and recent research findings in the field of cryptography.
- Crypto101: A free introductory book on cryptography, perfect for beginners and those looking to refresh their foundational knowledge.
- Cryptology ePrint Archive: An online repository of cryptology papers, where researchers from around the world share their latest findings and breakthroughs.
Top Cryptography Journals and Their Focus
- Journal Name: Journal of Cryptology
- Focus Area: Theoretical and practical aspects of cryptology
- Journal Name: Designs, Codes, and Cryptography
- Focus Area: Cryptographic algorithms and protocols
- Journal Name: IEEE Transactions on Information Forensics and Security
- Focus Area: Cryptographic applications in information security
The Role of Community Forums and Expert Discussions
- Crypto Stack Exchange: A Q&A platform dedicated to cryptographers, mathematicians, and others interested in cryptography. It’s a great place to ask questions, share knowledge, and learn from experts.
- Reddit’s r/crypto: A community-driven forum where enthusiasts discuss the latest trends, news, and breakthroughs in cryptography.
- Cryptography Mailing List: An email-based platform where researchers and professionals discuss and share the latest in cryptographic research.
Online Courses and Workshops
- Coursera’s Cryptography Specialization: Offered by Stanford University, this course covers the basics of cryptography to advanced topics like public-key cryptography and digital signatures.
- MIT OpenCourseWare (OCW) Cryptography and Cryptanalysis: A free course that delves deep into the mathematical aspects of cryptography.
- Workshops and Conferences: Regularly attending workshops, webinars, and conferences can provide hands-on experience and insights into the latest trends and research. Events like the RSA Conference and Black Hat are renowned for their in-depth sessions on encryption and cybersecurity.
The Future of Encryption
As we stand on the precipice of a new era in digital security, it’s essential to gaze into the horizon and anticipate the future of encryption. With the rapid advancements in technology, especially in fields like quantum computing, the encryption landscape is set to undergo significant transformations. This section will explore some predictions and potential developments in the realm of encryption.
Predictions about the Next Big Thing in Encryption

- Post-Quantum Cryptography: With the looming threat of quantum computers breaking current encryption standards, post-quantum cryptography is set to take center stage. These algorithms are being designed to resist quantum attacks, ensuring data security even in a post-quantum world.
- Homomorphic Encryption: A revolutionary concept, homomorphic encryption allows computations on encrypted data without decrypting it first. This means that sensitive data can remain encrypted while still being processed, offering unprecedented levels of security, especially for cloud computing.
- AI-Powered Encryption: As artificial intelligence continues to evolve, its integration with encryption is inevitable. AI can potentially optimize encryption processes, detect vulnerabilities, and even predict potential threats.
The Potential of Post-Quantum Encryption
As mentioned earlier, post-quantum encryption aims to provide security against quantum attacks. Several algorithms are currently under scrutiny, including:
- Lattice-Based Cryptography: Relies on the hardness of certain problems in lattice structures, believed to be resistant to quantum attacks.
- Hash-Based Cryptography: Uses cryptographic hash functions to create secure digital signatures.
- Code-Based Cryptography: Leverages the difficulty of decoding randomly generated linear codes.
Each of these methods offers a unique approach to encryption, and researchers are working diligently to determine the most secure and efficient techniques for the future.
Quantum-Resistant Algorithms: The New Gold Standard?
The encryption community actively prepares for the full potential of quantum computers. They are developing quantum-resistant algorithms to secure our data, even if quantum computers become mainstream. These algorithms, built from the ground up, resist both classical and quantum threats and could set a new gold standard in encryption.
Conclusion
The realm of encryption stands as a testament to human innovation, reflecting our deep-rooted desire for privacy and our resilience against ever-evolving cyber threats. From ancient ciphers to cutting-edge quantum-resistant algorithms, encryption has consistently been our shield in the digital world. As individuals, businesses, and governments navigate the complexities of the digital age, staying updated with encryption trends is not just beneficial—it’s imperative. This continuous evolution underscores the importance of proactive learning, ensuring that as the digital landscape shifts, we remain well-equipped to safeguard our data and digital identities.
As we look to the future, the story of encryption is far from over. It’s a narrative that each of us contributes to, shaping a secure digital future. Whether you’re a student, professional, or a curious individual, understanding encryption is a step towards becoming an informed digital citizen, capable of making better choices in an interconnected world.


Leave a Reply